Use the client-server API to isolate the Crypto hardware from non-secure application access.
The functions and other declarations used in this part of the driver are in cy_crypto.h and cy_crypto_server.h. You can also include cy_pdl.h to get access to all functions and declarations in the PDL.
The firmware initializes and starts the Crypto server. The server can run on any core and works with the Crypto hardware. The Crypto server is implemented as a secure block. It performs all cryptographic operations for the client. Access to the server is through the Inter Process Communication (IPC) driver. Direct access is not allowed.
The Crypto client can run on any core too. The firmware initializes and starts the client. The firmware then provides configuration data required for the desired cryptographic technique and a request that the server run the cryptographic operation.
This document contains the following topics:
The client-server implementation uses:
Firmware initializes and starts the Crypto server. The server can run on any core and works with the Crypto hardware. The Crypto server is implemented as a secure block. It performs all cryptographic operations for the client. Access to the server is through the Inter Process Communication (IPC) driver. Direct access is not allowed.
The Crypto client can also run on any core. Firmware initializes and starts the client. The firmware then provides the configuration data required for the desired cryptographic technique, and requests that the server run the cryptographic operation.
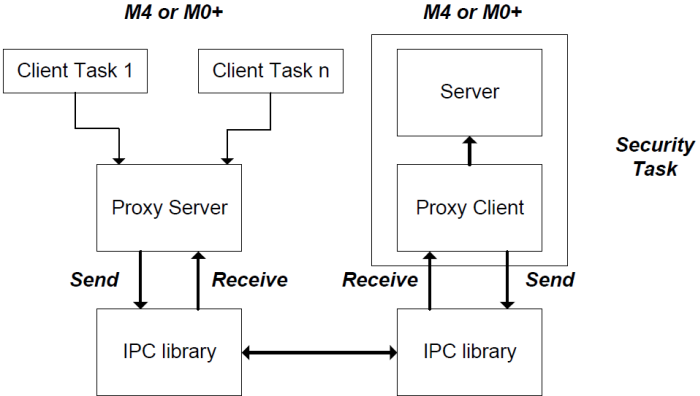
IPC communication between the client and server is completely transparent. Using IPC for communication provides a simple synchronization mechanism to handle concurrent requests from different cores.
IPC communication for the Crypto driver is handled transparently. User should select the IPC channel, and configure the required notify, release, and error interrupts.
These initialization routines, Cy_Crypto_Server_Start_Base, Cy_Crypto_Server_Start_Extra or Cy_Crypto_Server_Start_Full (server) and Cy_Crypto_Init (client), use separate instances of the same cy_stc_crypto_config_t configuration structure. Some fields should be the same, and some are set specifically by either the server or client. The table lists each field in the config structure, and which initialization routine sets the value.
| Field | Which | Description | Notes |
|---|---|---|---|
| ipcChannel | Server and Client | IPC channel for communication between client and server | IPC Channel, same for both |
| acquireNotifierChannel | Server and Client | IPC interrupt structure used for the new request notifications | Notify interrupt number, for Server side only |
| releaseNotifierChannel | Server and Client | IPC interrupt structure used for data ready notifications. Used to call userCompleteCallback handler function. | Release interrupt number, for Client side only |
| userCompleteCallback | Client | User-defined callback for the Release interrupt handler; can be NULL | See Implementing Crypto Interrupts |
| releaseNotifierConfig | Client | IRQ handler settings for data ready notifications. This interrupt occurs when server completely processed all input data and released an IPC communication channel. | configuration for the interrupt |
| userGetDataHandler | Server | User-defined function to override default interrupt handler; NULL = use default | ISR for the Notify interrupt |
| acquireNotifierConfig | Server | IRQ handler settings for new request notifications. This interrupt occurs when client sent a new request for processing. | configuration for the interrupt |
| userErrorHandler | Server | User-defined function to override default interrupt handler; NULL = use default | ISR for a server error |
| cryptoErrorIntrConfig | Server | IRQ handler settings for hardware error events | configuration for the interrupt |
Use a Crypto Server Start function (one of Cy_Crypto_Server_Start_Base, Cy_Crypto_Server_Start_Extra or Cy_Crypto_Server_Start_Full). Provide the configuration parameters (cy_stc_crypto_config_t) and a pointer to the server context (cy_stc_crypto_server_context_t) that will be used to store all temporary data.
Because the two cores operate asynchronously, ensure that server initialization is complete before initializing the client. There are several ways to do this:
All crypto operations are asynchronous. To ensure that any crypto operation is complete and the result is valid, use Cy_Crypto_Sync. Use the CY_CRYPTO_SYNC_NON_BLOCKING parameter to check status. Use CY_CRYPTO_SYNC_BLOCKING to wait for the operation to complete.
Use Cy_Crypto_Init to initialize the Crypto client with the configuration parameters (cy_stc_crypto_config_t) and a pointer to the context (cy_stc_crypto_context_t). Do not fill in the values for the context structure.
Then call Cy_Crypto_Enable to enable the Crypto hardware IP block. After this, the Crypto driver is ready to execute crypto functions. These calls must be made on the client side. Firmware can implement the client on either core.
To calculate CRC of a data image:
Code example:
To generate a pseudo random number:
Code example:
To generate a true random number:
Code example:
To encrypt a message using the DES algorithm:
Code example:
To encrypt a message using the TDES algorithm:
Code example:
The Crypto driver provides a four AES encryption algorithms (ECB, CBC, CFB and CTR) that are used similarly.
To encrypt a message using AES ECB algorithm (as example):
Code example:
To calculate a SHA digest of a message:
Code example:
To calculate CMAC of a message:
Code example:
To calculate HMAC of a message:
Code example:
To verify the RSA signature of the data image:
Code example:
General RSA encryption and decryption is supported. Cy_Crypto_Rsa_Proc encrypts or decrypts data based on the parameters passed to the function. If you pass in plain text and a public key, the output is encrypted (cipher text). If you pass in cipher text and a private key, the output is decrypted (plain text).
One parameter for this function call is a structure that defines the key: cy_stc_crypto_rsa_pub_key_t. The four modulus and exponent fields are mandatory. They represent the data for either the public or private key as appropriate.
The remaining fields represent three pre-calculated coefficients that can reduce execution time by up to 5x. The fields are: coefficient for Barrett reduction, binary inverse of the modulus, and the result of (2^moduloLength mod modulo). These fields are optional, and can be set to NULL.
Calculate these coefficients with Cy_Crypto_Rsa_CalcCoefs. Pass them in the address of the key structure with the modulus and exponent values for the key. The function returns the coefficients for the key in the key structure, replacing any previous values.
The RSA functionality also implements functions to decrypt a signature using a public key. This signature must follow the RSASSA-PKCS-v1_5 standard. The signature must contain a SHA digest (hash). MD2, MD4, and MD5 message digests are not supported.
An encrypted signature is stored as big-endian data. It must be inverted for RSA processing. To use the provided signature decryption, firmware must
The Crypto driver uses three interrupts:
You can modify default behavior for each interrupt.
Notify Interrupt: the Crypto server has a default ISR to handle this interrupt, Cy_Crypto_Server_GetDataHandler. The default ISR clears the interrupt, retrieves the data from the IPC channel, and dispatches control to the desired cryptographic operation.
To use the default handler, set the userGetDataHandler field of the cy_stc_crypto_config_t structure to NULL.
To override, populate this field with your ISR. Then call Crypto Server Start function. Your ISR can perform additional tasks required by your application logic, but must also call Cy_Crypto_Server_GetDataHandler to dispatch the data to the correct cryptographic operation.
Release Interrupt: The Crypto driver includes a handler for this interrupt. The interrupt handler clears the interrupt and calls a user-provided callback routine. You cannot override this interrupt handler. By default the interrupt is disabled.
To use default behavior (interrupt disabled), set the userCompleteCallback field of the cy_stc_crypto_config_t structure to NULL. To enable the interrupt, populate this field with your callback function. Then call Cy_Crypto_Init. If the callback function is not NULL, the Init function enables the interrupt, and default behavior calls your routine.
When performing cryptographic operations, firmware must ensure the operation is complete before acting on the results. If the release interrupt is disabled, typically calls to Cy_Crypto_Sync should be blocking. If the interrupt is enabled, your callback function is called when the operation is complete. This lets you avoid blocking calls to Cy_Crypto_Sync.
Error Interrupt: The Crypto server has a default ISR to handle this interrupt. It clears the interrupt and sets an internal flag that an error has occurred.
To use the default handler, set the userErrorHandler field of the cy_stc_crypto_config_t structure to NULL. To override, populate this field with your ISR. Then call Crypto Server Start function.
Your ISR must call Cy_Crypto_Server_ErrorHandler, and can perform any additional tasks required by your application logic.
API Reference | |
| Macros | |
| Functions | |
| Data Structures | |