Provides device startup, system configuration, and linker script files.
The system startup provides the followings features:
Allocation of different types of memory such as the ROM, flash and RAM etc. for the CPU is defined by the linker scripts.
For CYW20829
ARM GCC
The ROM, flash and RAM sections for the CPU are defined in the linker file: 'cyw20829_ns_flash_cbus.ld', where 'ns' indicates that the linker script file is for non-secure image. For devices without security extension, there will be only one linker file and it is always non-secure.
Memory sections are for the GNU GCC ARM tool set is defined in the linker file cyw20829_ns_flash_cbus.ld. Following are the important memory sections for the User/Application image.
Memory sections are for the GNU GCC ARM tool set is defined in the linker file <device>_ns.sct. Following are the important memory sections for the User/Application image.
ARM Compiler
The ROM, flash and RAM sections for the CPU are defined in the linker file: 'cyw20829_ns_flash_cbus.sct', where 'ns' indicates that the linker script file is for non-secure image. For devices without security extension, there will be only one linker file and it is always non-secure.
Memory sections are for the GNU GCC ARM tool set is defined in the linker file cyw20829_ns_flash_cbus.sct. Following are the important memory sections for the User/Application image.
IAR
The ROM, flash and RAM sections for the CPU are defined in the linker file: 'cyw20829_ns_flash_cbus.icf', where 'ns' indicates that the linker script file is for non-secure image. For devices without security extension, there will be only one linker file and it is always non-secure.
Memory sections are for the GNU GCC ARM tool set is defined in the linker file cyw20829_ns_flash_cbus.icf. Following are the important memory sections for the User/Application image.
CM33 Without ARM TrustZone Support:
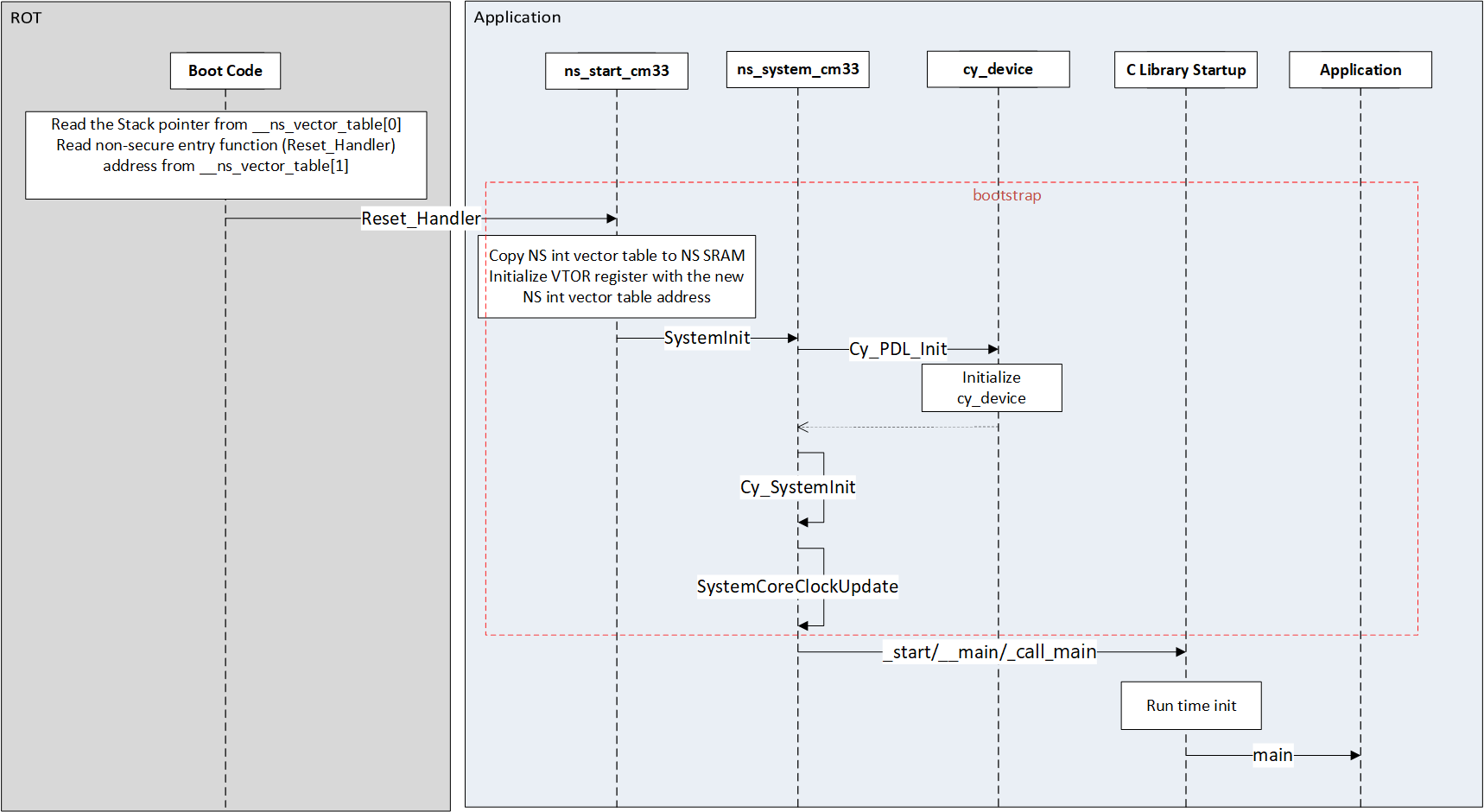
Below MSC describes the simplified startup sequence starting from reset release of the core. As soon as the reset is released, the execution starts form the ROM interrupt vector table reset vector. The ROM code initializes the basic clock needed to access and configure MMIO registers and then sets up debug port so that the debugger can be attached. After it finishes all the necessary initialization, it reads the bootstrap (part of non secure application image) location, size from TOC2 header and loads the bootstrap code into SRAM.
Before switching execution to the non-secure application code, the ROM code needs to initialize the stack pointer MSP_NS for the non-secure code. This value is picked form the first entry in the non-secure bootstrap's vector table __ns_vector_table. Once the non-secure stack is initialized, the ROM code will call the non-secure code entry point which is nothing but the Reset_Handler. Address of this function is picked form the second entry in the non-secure vector table __ns_vector_table and type casting it to function pointer.
In the non-secure Reset_Handler, the vector table is copied to RAM area and then the address of the vector table is set to VTOR register. This calls SystemInit function which internally calls Cy_PDL_Init, Cy_SystemInit and SystemCoreClockUpdate functions. Then it calls C runtime initialization function which calls main function of the application code.
Below sequence diagram captures the initialization process in the startup code.
By default, the stack size is set to 0x00001000 and the entire remaining ram is used for the heap
The default interrupt handler functions are dummy handler in the startup file.
Below is the default handler for the non-secure interrupts:
This process uses memory sections defined in the linker script. The startup code copies the default vector table contents to the non-secure SRAM region specified by the linker script. APIs are provided in the sysint driver to hook user implemented handler replacing the default handler for the corresponding interrupt.
Following tables provide the address of the default and non-secure SRAM interrupt vector table for different supported compilers.
The linker script file is 'cyw20829_ns_flash_cbus.ld'. For non-secure world, it uses the following variable.
Copy interrupt vectors from ROM/flash to RAM:
From:
To:
The vector table address (and the vector table itself) are defined in the ns_start_<device>.c startup file corresponding to non-secure world. The code in these files copies the vector table from ROM/Flash to RAM.
The linker script file is 'cyw20829_ns_flash_cbus.sct'. For non-secure world, it uses the following variable.
Copy interrupt vectors from ROM/flash to RAM:
From:
To:
The vector table address (and the vector table itself) are defined in the ns_start_<device>.c startup file corresponding to non-secure world. The code in these files copies the vector table from ROM/Flash to RAM.
The linker script file is 'cyw20829_ns_flash_cbus.icf'. For non-secure world, it uses the following variable.
Copy interrupt vectors from ROM/flash to RAM:
From:
To:
The vector table address (and the vector table itself) are defined in the ns_start_<device>.c startup file corresponding to non-secure worlds. The code in these files copies the vector table from ROM/Flash to RAM.
| Version | Changes | Reason for Change |
|---|---|---|
| 1.2 | Added new internal functions. | Added support for DSRAM Setup for CAT1B devices. |
| 1.1 | Restructured documentation and internal function behaviour. | User experience enhancement. |
| 1.0 | Initial version |
API Reference | |
| Macros | |