This file implements the OPTIGA Crypt module. More...
#include "optiga_crypt.h"#include "optiga_lib_logger.h"#include "optiga_lib_common_internal.h"#include "pal_os_memory.h"
| #define | OPTIGA_CRYPT_ECDSA_FIPS_186_3_WITHOUT_HASH (0x11) |
| ECDSA FIPS 186-3 without hash. More... | |
| #define | OPTIGA_CRYPT_ECDH_KEY_AGREEMENT_ALGORITHM (0x01) |
| Elliptic Curve Diffie-Hellman key agreement algorithm. More... | |
| #define | OPTIGA_CRYPT_MINIMUM_RANDOM_DATA_LENGTH (0x08) |
| Minimum length of random data. More... | |
| #define | OPTIGA_CRYTP_RANDOM_PARAM_PRE_MASTER_SECRET (0x04) |
| Param type for optiga pre-master secret. More... | |
| #define | OPTIGA_CRYTP_MINIMUM_OPTIONAL_DATA_LENGTH (0x28) |
| Minimum optional data length. More... | |
| _STATIC_H void | optiga_crypt_generic_event_handler (void *p_ctx, optiga_lib_status_t event) |
| _STATIC_H void | optiga_crypt_reset_protection_level (optiga_crypt_t *me) |
| void | optiga_cmd_set_shielded_connection_option (optiga_cmd_t *me, uint8_t value, uint8_t shielded_connection_option) |
| _STATIC_H optiga_lib_status_t | optiga_crypt_generate_keypair (optiga_crypt_t *me, uint8_t cmd_param, uint8_t key_usage, bool_t export_private_key, void *p_private_key, uint8_t *p_public_key, uint16_t *p_public_key_length) |
| _STATIC_H optiga_lib_status_t | optiga_crypt_sign (optiga_crypt_t *me, uint8_t signature_scheme, const uint8_t *p_digest, uint8_t digest_length, optiga_key_id_t private_key, uint8_t *p_signature, uint16_t *p_signature_length, uint16_t salt_length) |
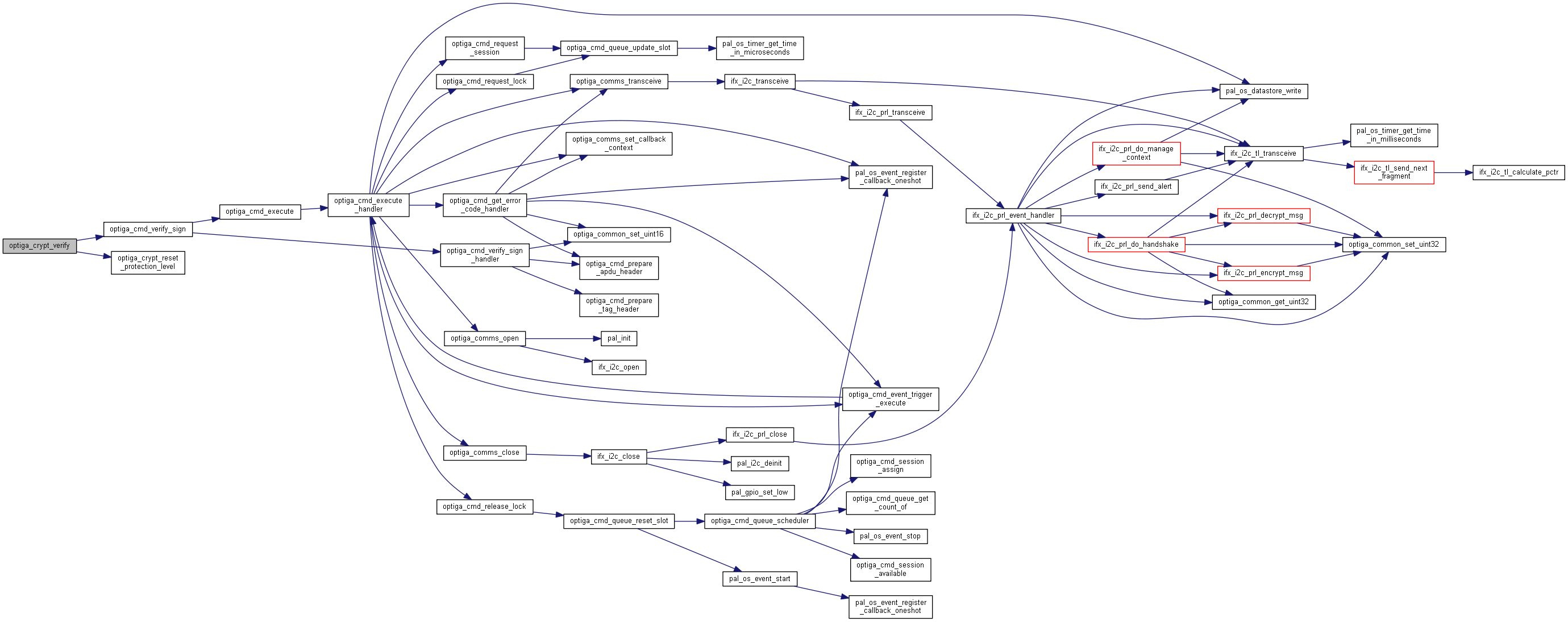
| _STATIC_H optiga_lib_status_t | optiga_crypt_verify (optiga_crypt_t *me, uint8_t cmd_param, const uint8_t *p_digest, uint8_t digest_length, const uint8_t *p_signature, uint16_t signature_length, uint8_t public_key_source_type, const void *p_public_key, uint16_t salt_length) |
| _STATIC_H optiga_lib_status_t | optiga_crypt_rsa_enc_dec (optiga_crypt_t *me, optiga_rsa_encryption_scheme_t encryption_scheme, const uint8_t *p_message, uint16_t message_length, const uint8_t *p_label, uint16_t label_length, uint8_t public_key_source_type, const void *p_key, uint8_t *p_processed_message, uint16_t *p_processed_message_length, bool_t is_enc) |
| _STATIC_H optiga_lib_status_t | optiga_crypt_get_random (optiga_crypt_t *me, uint8_t cmd_param, uint8_t *p_random_data, uint16_t random_data_length, const uint8_t *p_optional_data, uint16_t optional_data_length) |
| void | optiga_crypt_set_comms_params (optiga_crypt_t *me, uint8_t parameter_type, uint8_t value) |
| Sets/updates the OPTIGA Comms Shielded connection configuration in the respective (optiga_util) instance. More... | |
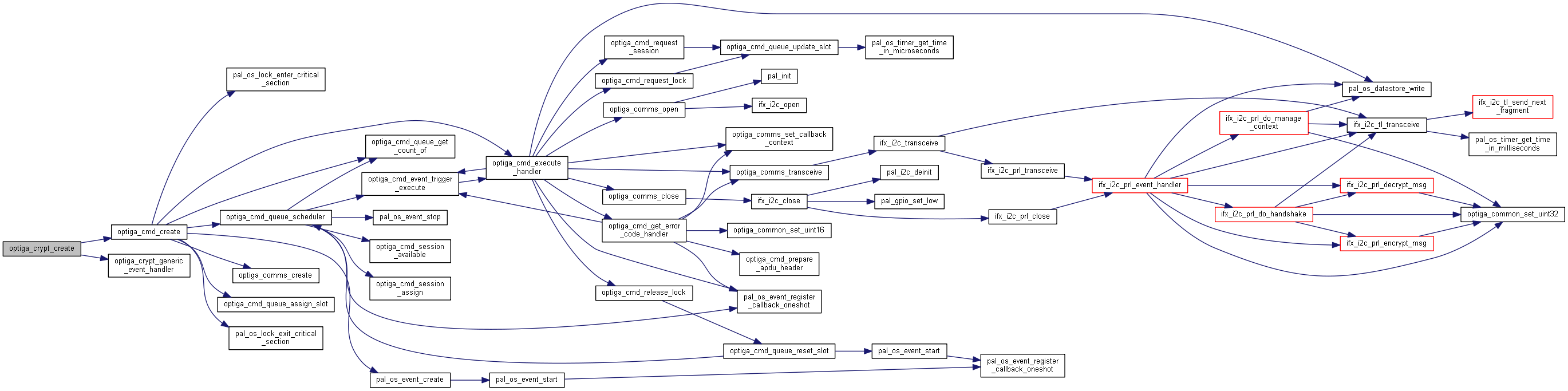
| optiga_crypt_t * | optiga_crypt_create (uint8_t optiga_instance_id, callback_handler_t handler, void *caller_context) |
| Create an instance of optiga_crypt_t. More... | |
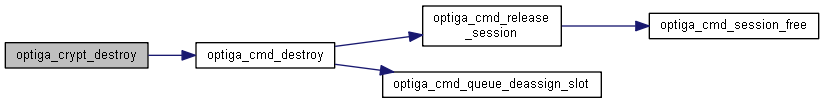
| optiga_lib_status_t | optiga_crypt_destroy (optiga_crypt_t *me) |
| Destroys an instance of optiga_crypt_t. More... | |
| optiga_lib_status_t | optiga_crypt_random (optiga_crypt_t *me, optiga_rng_type_t rng_type, uint8_t *random_data, uint16_t random_data_length) |
| Generates a random number. More... | |
| optiga_lib_status_t | optiga_crypt_hash_start (optiga_crypt_t *me, optiga_hash_context_t *hash_ctx) |
| Initializes a hash context. More... | |
| optiga_lib_status_t | optiga_crypt_hash_update (optiga_crypt_t *me, optiga_hash_context_t *hash_ctx, uint8_t source_of_data_to_hash, const void *data_to_hash) |
| Updates a hash context with the input data. More... | |
| optiga_lib_status_t | optiga_crypt_hash_finalize (optiga_crypt_t *me, optiga_hash_context_t *hash_ctx, uint8_t *hash_output) |
| Finalizes and exports the hash output. More... | |
| optiga_lib_status_t | optiga_crypt_ecc_generate_keypair (optiga_crypt_t *me, optiga_ecc_curve_t curve_id, uint8_t key_usage, bool_t export_private_key, void *private_key, uint8_t *public_key, uint16_t *public_key_length) |
| Generates an key pair based on ECC curves. More... | |
| optiga_lib_status_t | optiga_crypt_ecdsa_sign (optiga_crypt_t *me, const uint8_t *digest, uint8_t digest_length, optiga_key_id_t private_key, uint8_t *signature, uint16_t *signature_length) |
| Generates a signature for the given digest. More... | |
| optiga_lib_status_t | optiga_crypt_ecdsa_verify (optiga_crypt_t *me, const uint8_t *digest, uint8_t digest_length, const uint8_t *signature, uint16_t signature_length, uint8_t public_key_source_type, const void *public_key) |
| Verifies the signature over the given digest. More... | |
| optiga_lib_status_t | optiga_crypt_ecdh (optiga_crypt_t *me, optiga_key_id_t private_key, public_key_from_host_t *public_key, bool_t export_to_host, uint8_t *shared_secret) |
| Calculates the shared secret using ECDH algorithm. More... | |
| optiga_lib_status_t | optiga_crypt_tls_prf_sha256 (optiga_crypt_t *me, uint16_t secret, const uint8_t *label, uint16_t label_length, const uint8_t *seed, uint16_t seed_length, uint16_t derived_key_length, bool_t export_to_host, uint8_t *derived_key) |
| Derives a key. More... | |
| optiga_lib_status_t | optiga_crypt_rsa_generate_keypair (optiga_crypt_t *me, optiga_rsa_key_type_t key_type, uint8_t key_usage, bool_t export_private_key, void *private_key, uint8_t *public_key, uint16_t *public_key_length) |
| Generates an key pair based on RSA key type. More... | |
| optiga_lib_status_t | optiga_crypt_rsa_sign (optiga_crypt_t *me, optiga_rsa_signature_scheme_t signature_scheme, const uint8_t *digest, uint8_t digest_length, optiga_key_id_t private_key, uint8_t *signature, uint16_t *signature_length, uint16_t salt_length) |
| Generates a RSA signature for the given digest based on the input signature scheme. More... | |
| optiga_lib_status_t | optiga_crypt_rsa_verify (optiga_crypt_t *me, optiga_rsa_signature_scheme_t signature_scheme, const uint8_t *digest, uint8_t digest_length, const uint8_t *signature, uint16_t signature_length, uint8_t public_key_source_type, const void *public_key, uint16_t salt_length) |
| Verifies the RSA signature over the given digest. More... | |
| optiga_lib_status_t | optiga_crypt_rsa_encrypt_message (optiga_crypt_t *me, optiga_rsa_encryption_scheme_t encryption_scheme, const uint8_t *message, uint16_t message_length, const uint8_t *label, uint16_t label_length, uint8_t public_key_source_type, const void *public_key, uint8_t *encrypted_message, uint16_t *encrypted_message_length) |
| Encrypts message using RSA public key. More... | |
| optiga_lib_status_t | optiga_crypt_rsa_encrypt_session (optiga_crypt_t *me, optiga_rsa_encryption_scheme_t encryption_scheme, const uint8_t *label, uint16_t label_length, uint8_t public_key_source_type, const void *public_key, uint8_t *encrypted_message, uint16_t *encrypted_message_length) |
| Encrypts session data using RSA public key. More... | |
| optiga_lib_status_t | optiga_crypt_rsa_decrypt_and_export (optiga_crypt_t *me, optiga_rsa_encryption_scheme_t encryption_scheme, const uint8_t *encrypted_message, uint16_t encrypted_message_length, const uint8_t *label, uint16_t label_length, optiga_key_id_t private_key, uint8_t *message, uint16_t *message_length) |
| Decrypts input data using OPTIGA private key and export it to the host. More... | |
| optiga_lib_status_t | optiga_crypt_rsa_decrypt_and_store (optiga_crypt_t *me, optiga_rsa_encryption_scheme_t encryption_scheme, const uint8_t *encrypted_message, uint16_t encrypted_message_length, const uint8_t *label, uint16_t label_length, optiga_key_id_t private_key) |
| Decrypts input data using OPTIGA private key and stores it in a OPTIGA session. More... | |
| optiga_lib_status_t | optiga_crypt_rsa_generate_pre_master_secret (optiga_crypt_t *me, const uint8_t *optional_data, uint16_t optional_data_length, uint16_t pre_master_secret_length) |
| Generates a pre-master secret. More... | |
This file implements the OPTIGA Crypt module.
Copyright (c) 2019 Infineon Technologies AG
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE
\endcopyright
| #define OPTIGA_CRYPT_ECDH_KEY_AGREEMENT_ALGORITHM (0x01) |
Elliptic Curve Diffie-Hellman key agreement algorithm.
| #define OPTIGA_CRYPT_ECDSA_FIPS_186_3_WITHOUT_HASH (0x11) |
ECDSA FIPS 186-3 without hash.
| #define OPTIGA_CRYPT_MINIMUM_RANDOM_DATA_LENGTH (0x08) |
Minimum length of random data.
| #define OPTIGA_CRYTP_MINIMUM_OPTIONAL_DATA_LENGTH (0x28) |
Minimum optional data length.
| #define OPTIGA_CRYTP_RANDOM_PARAM_PRE_MASTER_SECRET (0x04) |
Param type for optiga pre-master secret.
| void optiga_cmd_set_shielded_connection_option | ( | optiga_cmd_t * | me, |
| uint8_t | value, | ||
| uint8_t | shielded_connection_option | ||
| ) |
| optiga_crypt_t* optiga_crypt_create | ( | uint8_t | optiga_instance_id, |
| callback_handler_t | handler, | ||
| void * | caller_context | ||
| ) |
Create an instance of optiga_crypt_t.
Create an instance of optiga_crypt_t.
| [in] | optiga_instance_id | Indicates the OPTIGA instance to be associated with optiga_crypt_t. Should be defined as below: Use OPTIGA_INSTANCE_ID_0. |
| [in] | handler | Pointer to callback function, must not be NULL. |
| [in] | caller_context | Pointer to upper layer context. Contains user context data. |
| optiga_crypt_t | On success function will return pointer of optiga_crypt_t. |
| NULL | Input arguments are NULL. Low layer function fails. OPTIGA_CMD_MAX_REGISTRATIONS number of instances are already created. |
| optiga_lib_status_t optiga_crypt_destroy | ( | optiga_crypt_t * | me | ) |
Destroys an instance of optiga_crypt_t.
Destroys the optiga_crypt_t instance.
| [in] | me | Valid instance of optiga_crypt_t. |
| OPTIGA_LIB_SUCCESS | Successful invocation. |
| OPTIGA_CRYPT_ERROR_INVALID_INPUT | Wrong Input arguments provided. |
| OPTIGA_CRYPT_ERROR_INSTANCE_IN_USE | The previous operation with the same instance is not complete. |
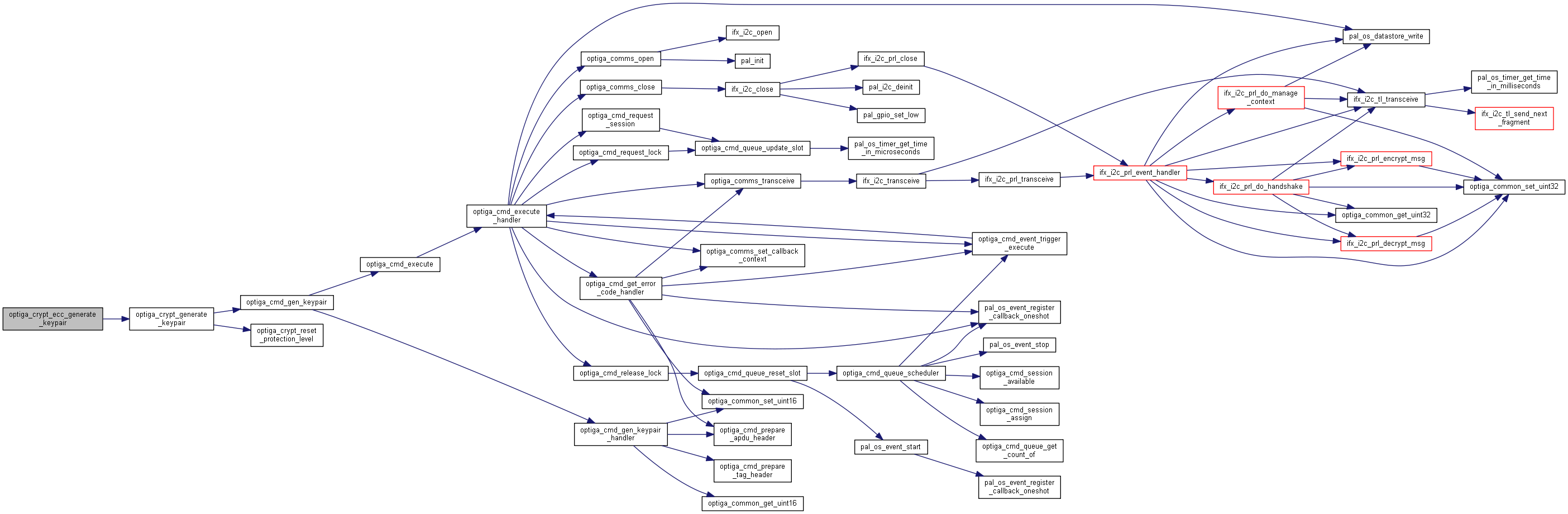
| optiga_lib_status_t optiga_crypt_ecc_generate_keypair | ( | optiga_crypt_t * | me, |
| optiga_ecc_curve_t | curve_id, | ||
| uint8_t | key_usage, | ||
| bool_t | export_private_key, | ||
| void * | private_key, | ||
| uint8_t * | public_key, | ||
| uint16_t * | public_key_length | ||
| ) |
Generates an key pair based on ECC curves.
Generates an ECC key-pair based on the type of the key.
| [in] | me | Valid instance of optiga_crypt_t created using optiga_crypt_create. |
| [in] | curve_id | ECC curve id. |
| [in] | key_usage | Key usage defined by optiga_key_usage_t.
|
| [in] | export_private_key | TRUE (1) or Non-Zero value - Exports private key to the host. FALSE (0) - Exports only public key to the host and writes private key to OPTIGA. The input key_usage is ignored. |
| [in] | private_key | Buffer to store private key or private key OID of OPTIGA, must not be NULL.
|
| [in,out] | public_key | Buffer to store public key, must not be NULL. |
| [in] | public_key_length | Initially set as length of public_key, later updated as actual length of public_key. |
| OPTIGA_CRYPT_SUCCESS | Successful invocation. |
| OPTIGA_CRYPT_ERROR_INVALID_INPUT | Wrong Input arguments provided. |
| OPTIGA_CRYPT_ERROR_INSTANCE_IN_USE | The previous operation with the same instance is not complete. |
| OPTIGA_DEVICE_ERROR | Command execution failure in OPTIGA and the LSB indicates the error code. (Refer Solution Reference Manual) |
Example
example_optiga_crypt_ecc_generate_keypair.c
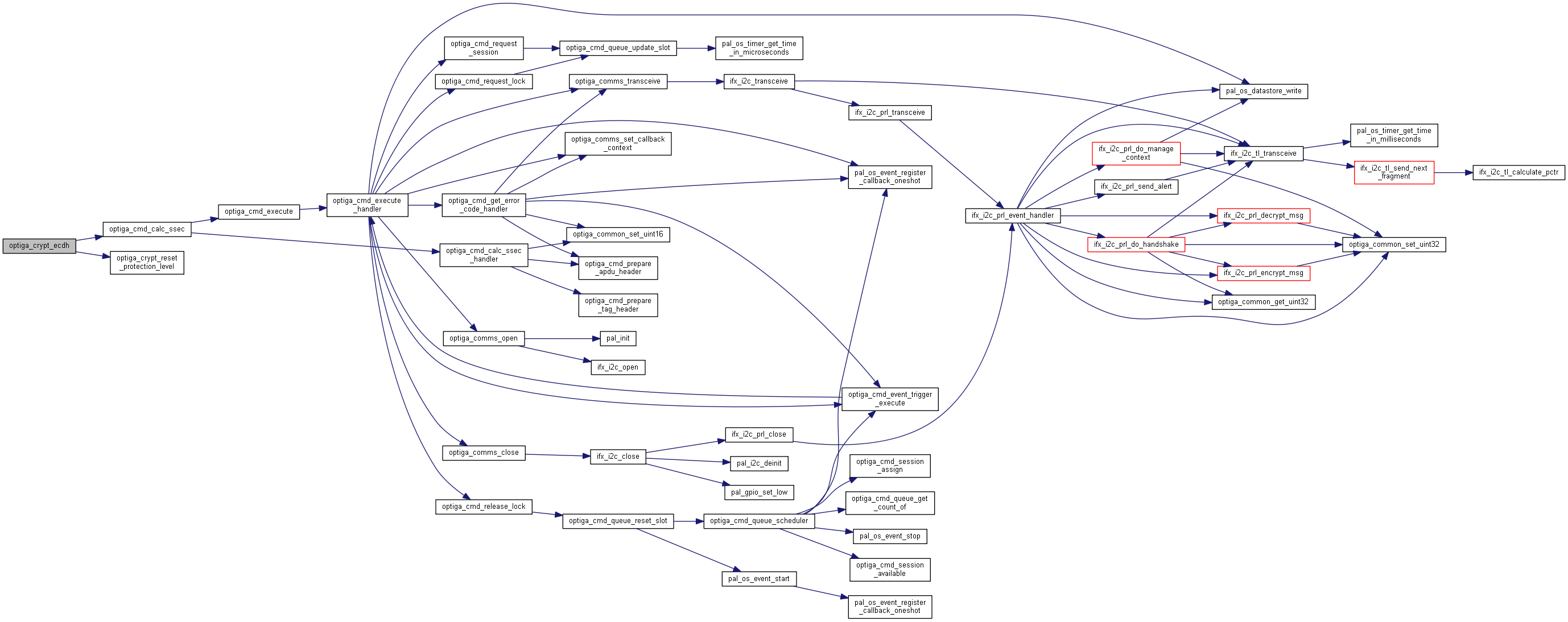
| optiga_lib_status_t optiga_crypt_ecdh | ( | optiga_crypt_t * | me, |
| optiga_key_id_t | private_key, | ||
| public_key_from_host_t * | public_key, | ||
| bool_t | export_to_host, | ||
| uint8_t * | shared_secret | ||
| ) |
Calculates the shared secret using ECDH algorithm.
Calculates the shared secret using ECDH algorithm
| [in] | me | Valid instance of optiga_crypt_t created using optiga_crypt_create. |
| [in] | private_key | Object ID of the private key stored in OPTIGA.
|
| [in] | public_key | Pointer to the public key structure for shared secret generation with its properties, must not be NULL.
|
| [in] | export_to_host | TRUE (1) or Non-Zero value - Exports the generated shared secret to Host. FALSE (0) - Stores the generated shared secret into the session object ID acquired by the instance. |
| [in,out] | shared_secret | Pointer to the shared secret buffer, only if export_to_host is TRUE. Otherwise provide NULL as input. |
| OPTIGA_CRYPT_SUCCESS | Successful invocation |
| OPTIGA_CRYPT_ERROR_INVALID_INPUT | Wrong Input arguments provided |
| OPTIGA_CRYPT_ERROR_INSTANCE_IN_USE | The previous operation with the same instance is not complete |
| OPTIGA_DEVICE_ERROR | Command execution failure in OPTIGA and the LSB indicates the error code. (Refer Solution Reference Manual) |
Example
example_optiga_crypt_ecdh.c
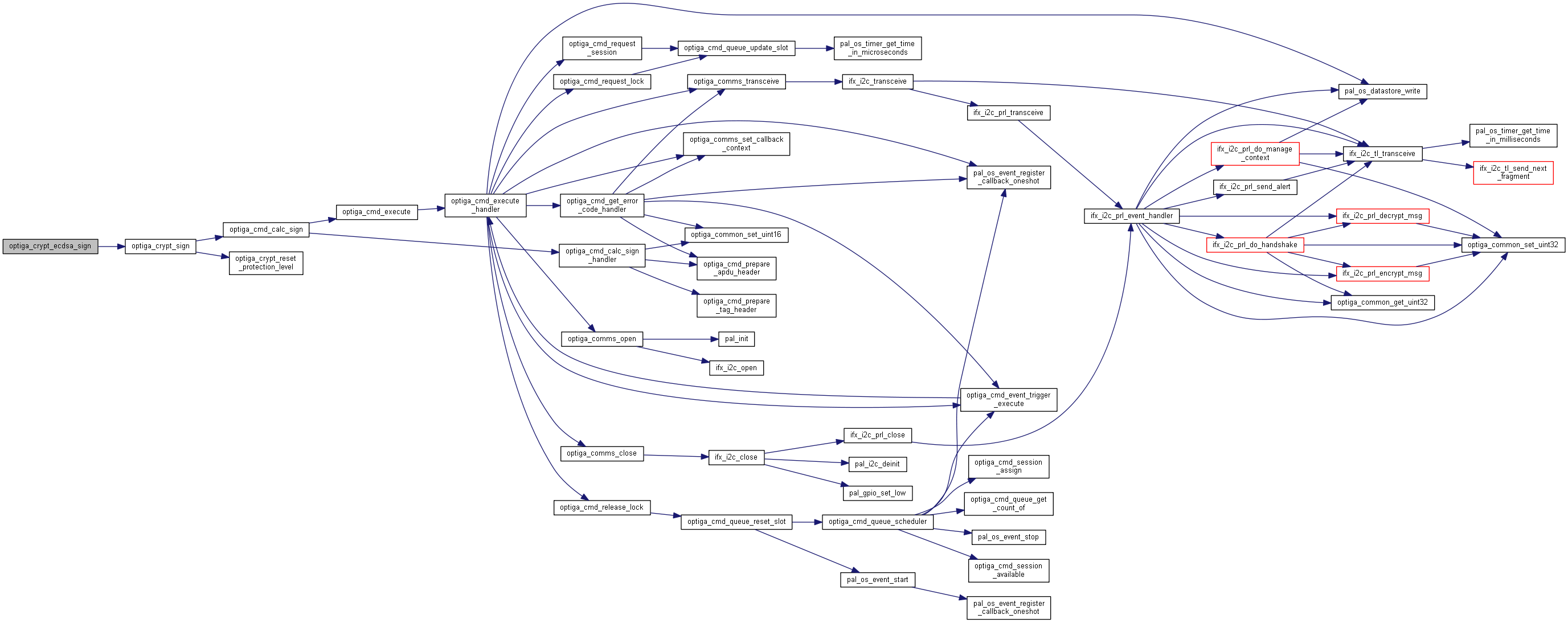
| optiga_lib_status_t optiga_crypt_ecdsa_sign | ( | optiga_crypt_t * | me, |
| const uint8_t * | digest, | ||
| uint8_t | digest_length, | ||
| optiga_key_id_t | private_key, | ||
| uint8_t * | signature, | ||
| uint16_t * | signature_length | ||
| ) |
Generates a signature for the given digest.
Generates a signature for the given digest using private key stored in OPTIGA.
| [in] | me | Valid instance of optiga_crypt_t created using optiga_crypt_create. |
| [in] | digest | Digest on which signature is generated. |
| [in] | digest_length | Length of the input digest. |
| [in] | private_key | Private key OID to generate signature. |
| [in,out] | signature | Pointer to store generated signature, must not be NULL.
|
| [in,out] | signature_length | Length of signature. Initial value set as length of buffer, later updated as the actual length of generated signature. |
| OPTIGA_CRYPT_SUCCESS | Successful invocation. |
| OPTIGA_CRYPT_ERROR_INVALID_INPUT | Wrong Input arguments provided. |
| OPTIGA_CRYPT_ERROR_INSTANCE_IN_USE | The previous operation with the same instance is not complete. |
| OPTIGA_DEVICE_ERROR | Command execution failure in OPTIGA and the LSB indicates the error code. (Refer Solution Reference Manual) |
Example
example_optiga_crypt_ecdsa_sign.c
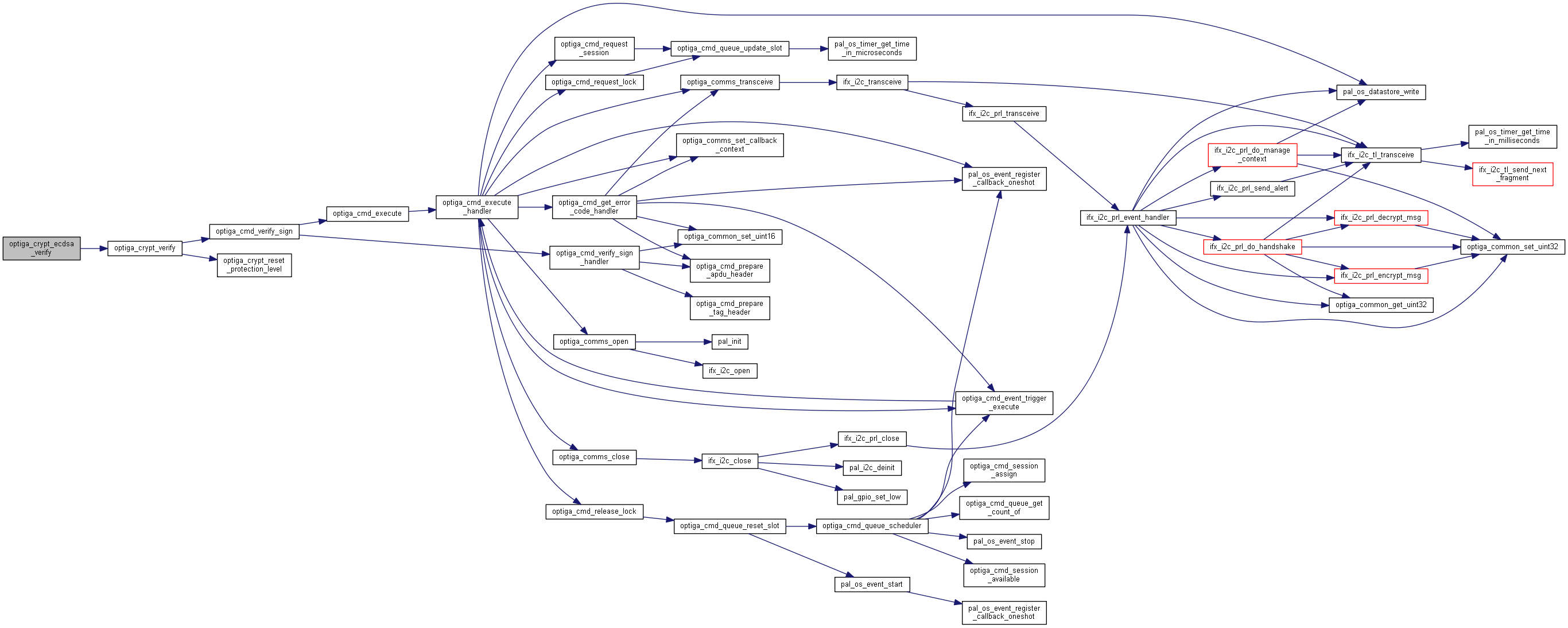
| optiga_lib_status_t optiga_crypt_ecdsa_verify | ( | optiga_crypt_t * | me, |
| const uint8_t * | digest, | ||
| uint8_t | digest_length, | ||
| const uint8_t * | signature, | ||
| uint16_t | signature_length, | ||
| uint8_t | public_key_source_type, | ||
| const void * | public_key | ||
| ) |
Verifies the signature over the given digest.
Verifies the signature over a given digest provided with the input data.
| [in] | me | Valid instance of optiga_crypt_t created using optiga_crypt_create. |
| [in] | digest | Pointer to a given digest buffer, must not be NULL. |
| [in] | digest_length | Length of digest. |
| [in] | signature | Pointer to a given signature buffer, must not be NULL. |
| [in] | signature_length | Length of signature. |
| [in] | public_key_source_type | Public key from host / public key of certificate OID from OPTIGA. Value must be one of the below
|
| [in] | public_key | Public key from host / OID of certificate object. Value must be one of the below
|
| OPTIGA_CRYPT_SUCCESS | Successful invocation |
| OPTIGA_CRYPT_ERROR_INVALID_INPUT | Wrong Input arguments provided |
| OPTIGA_CRYPT_ERROR_INSTANCE_IN_USE | The previous operation with the same instance is not complete |
| OPTIGA_DEVICE_ERROR | Command execution failure in OPTIGA and the LSB indicates the error code. (Refer Solution Reference Manual) |
Example
example_optiga_crypt_ecdsa_verify.c
| _STATIC_H optiga_lib_status_t optiga_crypt_generate_keypair | ( | optiga_crypt_t * | me, |
| uint8_t | cmd_param, | ||
| uint8_t | key_usage, | ||
| bool_t | export_private_key, | ||
| void * | p_private_key, | ||
| uint8_t * | p_public_key, | ||
| uint16_t * | p_public_key_length | ||
| ) |
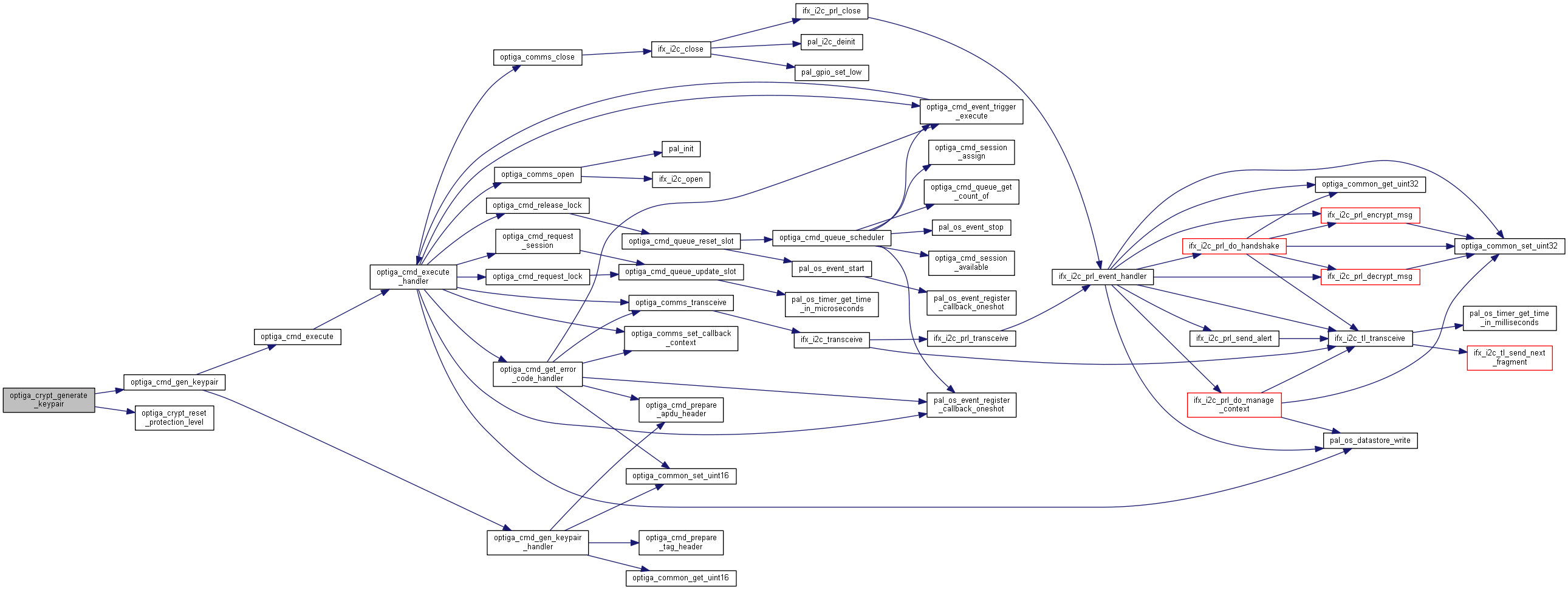
| _STATIC_H void optiga_crypt_generic_event_handler | ( | void * | p_ctx, |
| optiga_lib_status_t | event | ||
| ) |
| _STATIC_H optiga_lib_status_t optiga_crypt_get_random | ( | optiga_crypt_t * | me, |
| uint8_t | cmd_param, | ||
| uint8_t * | p_random_data, | ||
| uint16_t | random_data_length, | ||
| const uint8_t * | p_optional_data, | ||
| uint16_t | optional_data_length | ||
| ) |
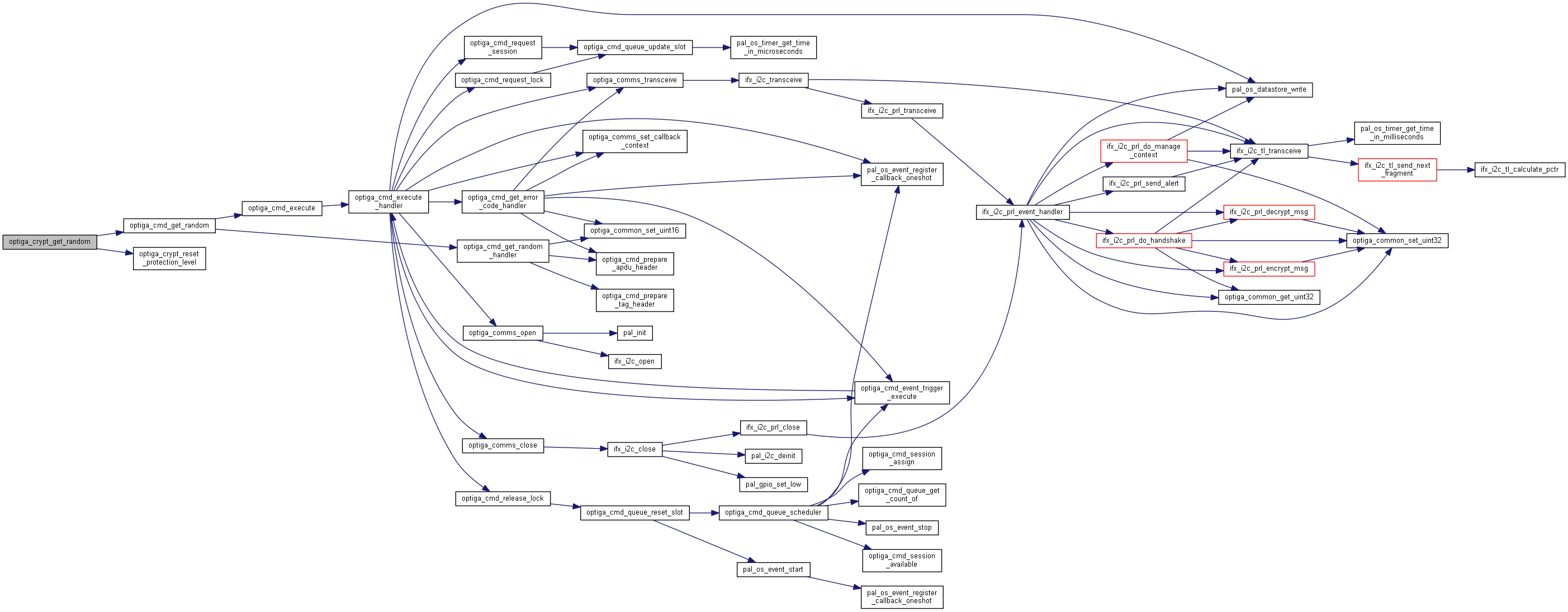
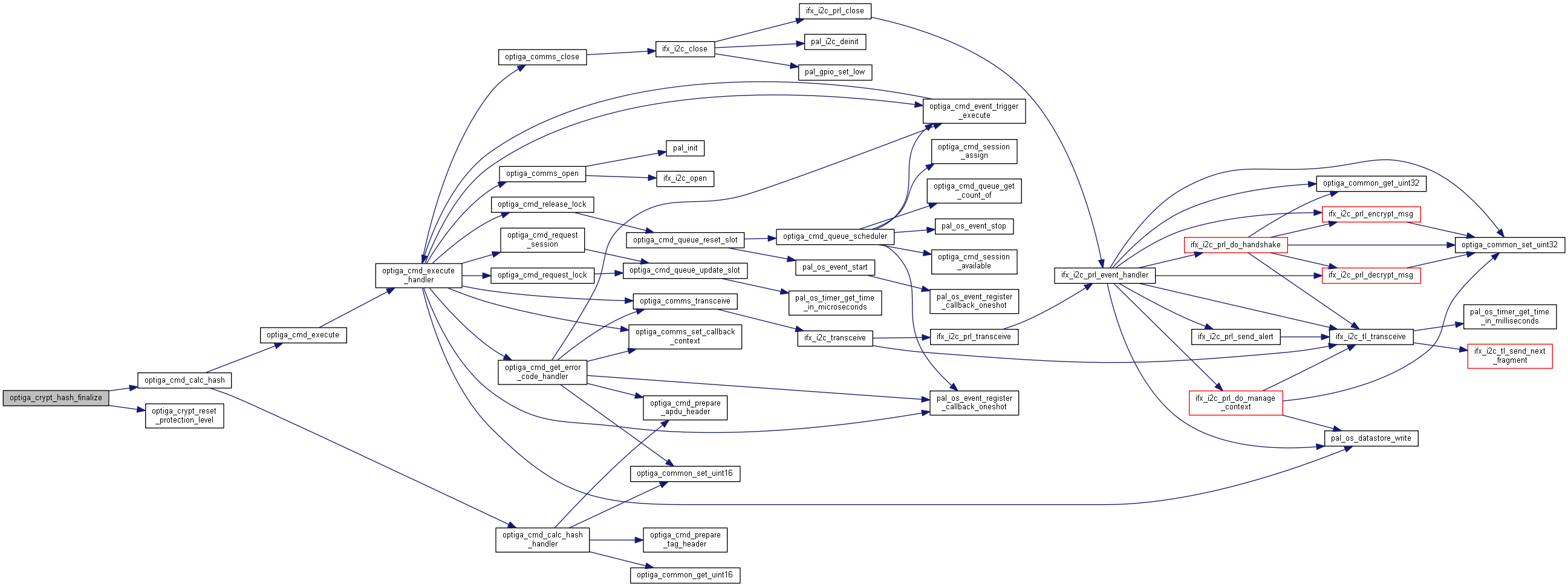
| optiga_lib_status_t optiga_crypt_hash_finalize | ( | optiga_crypt_t * | me, |
| optiga_hash_context_t * | hash_ctx, | ||
| uint8_t * | hash_output | ||
| ) |
Finalizes and exports the hash output.
Finalizes the hash context and returns hash as output.
| [in] | me | Valid instance of optiga_crypt_t created using optiga_crypt_create. |
| [in] | hash_ctx | Pointer to optiga_hash_context_t containing hash context from OPTIGA, must not be NULL. |
| [in,out] | hash_output | Output Hash. |
| OPTIGA_CRYPT_SUCCESS | Successful invocation. |
| OPTIGA_CRYPT_ERROR_INVALID_INPUT | Wrong Input arguments provided. |
| OPTIGA_CRYPT_ERROR_INSTANCE_IN_USE | The previous operation with the same instance is not complete. |
| OPTIGA_DEVICE_ERROR | Command execution failure in OPTIGA and the LSB indicates the error code. (Refer Solution Reference Manual) |
Example
example_optiga_crypt_hash.c
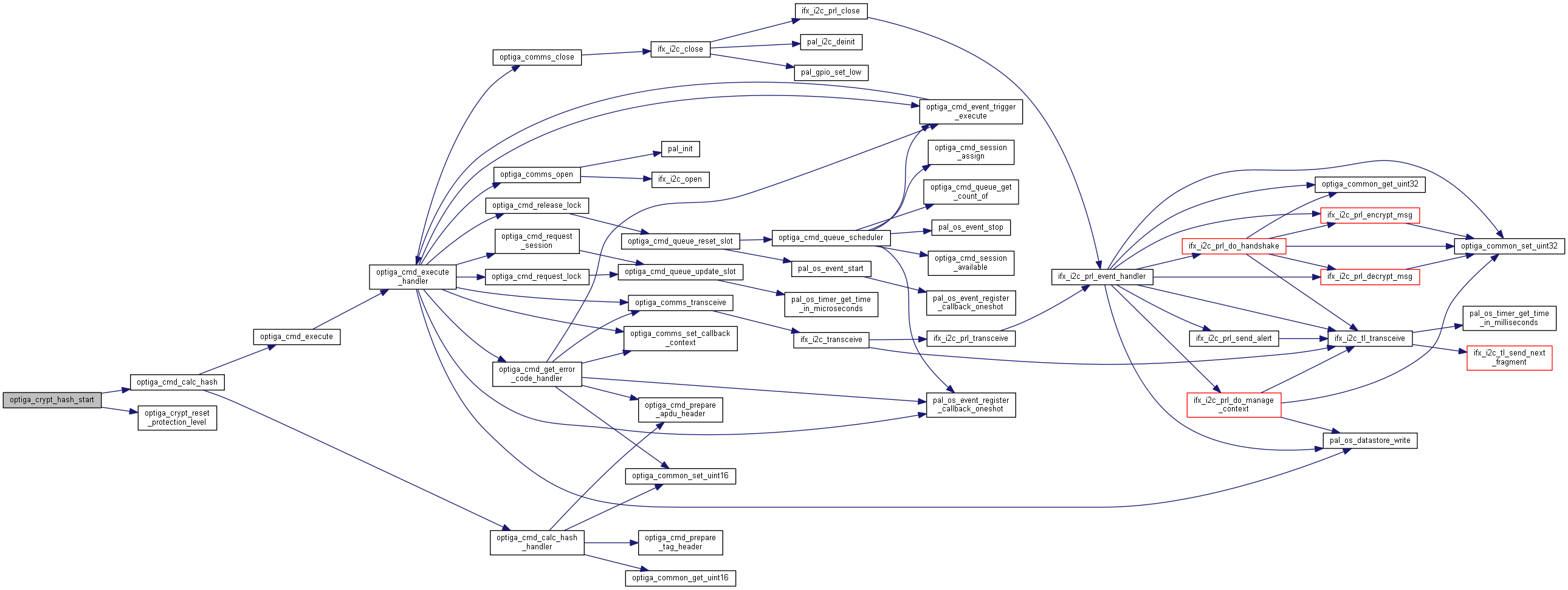
| optiga_lib_status_t optiga_crypt_hash_start | ( | optiga_crypt_t * | me, |
| optiga_hash_context_t * | hash_ctx | ||
| ) |
Initializes a hash context.
Sets up a hash context and exports it.
| [in] | me | Valid instance of optiga_crypt_t created using optiga_crypt_create. |
| [in,out] | hash_ctx | Pointer to optiga_hash_context_t to store the hash context from OPTIGA.
|
| OPTIGA_CRYPT_SUCCESS | Successful invocation. |
| OPTIGA_CRYPT_ERROR_INVALID_INPUT | Wrong Input arguments provided. |
| OPTIGA_CRYPT_ERROR_INSTANCE_IN_USE | The previous operation with the same instance is not complete. |
| OPTIGA_DEVICE_ERROR | Command execution failure in OPTIGA and the LSB indicates the error code. (Refer Solution Reference Manual) |
Example
example_optiga_crypt_hash.c
| optiga_lib_status_t optiga_crypt_hash_update | ( | optiga_crypt_t * | me, |
| optiga_hash_context_t * | hash_ctx, | ||
| uint8_t | source_of_data_to_hash, | ||
| const void * | data_to_hash | ||
| ) |
Updates a hash context with the input data.
Updates hashing for the given data and hash context then export the updated hash context.
| [in] | me | Valid instance of optiga_crypt_t created using optiga_crypt_create. |
| [in] | hash_ctx | Pointer to optiga_hash_context_t containing hash context from OPTIGA, must not be NULL |
| [in] | source_of_data_to_hash | Data from host / Data in optiga. Must be one of the below
|
| [in] | data_to_hash | Data for hashing either in hash_data_from_host or in hash_data_in_optiga |
| OPTIGA_CRYPT_SUCCESS | Successful invocation. |
| OPTIGA_CRYPT_ERROR_INVALID_INPUT | Wrong Input arguments provided. |
| OPTIGA_CRYPT_ERROR_INSTANCE_IN_USE | The previous operation with the same instance is not complete. |
| OPTIGA_DEVICE_ERROR | Command execution failure in OPTIGA and the LSB indicates the error code. (Refer Solution Reference Manual) |
Example
example_optiga_crypt_hash.c
| optiga_lib_status_t optiga_crypt_random | ( | optiga_crypt_t * | me, |
| optiga_rng_type_t | rng_type, | ||
| uint8_t * | random_data, | ||
| uint16_t | random_data_length | ||
| ) |
Generates a random number.
Generates the requested random stream of data for the user provided length.
| [in] | me | Valid instance of optiga_crypt_t created using optiga_crypt_create. |
| [in] | rng_type | Type of random data generator.
|
| [in,out] | random_data | Pointer to the buffer into which random data is stored, must not be NULL. |
| [in] | random_data_length | Length of random data to be generated.
|
| OPTIGA_CRYPT_SUCCESS | Successful invocation. |
| OPTIGA_CRYPT_ERROR_INVALID_INPUT | Wrong Input arguments provided. |
| OPTIGA_CRYPT_ERROR_INSTANCE_IN_USE | The previous operation with the same instance is not complete. |
| OPTIGA_DEVICE_ERROR | Command execution failure in OPTIGA and the LSB indicates the error code. (Refer Solution Reference Manual) |
Example
example_optiga_crypt_random.c
| _STATIC_H void optiga_crypt_reset_protection_level | ( | optiga_crypt_t * | me | ) |
| optiga_lib_status_t optiga_crypt_rsa_decrypt_and_export | ( | optiga_crypt_t * | me, |
| optiga_rsa_encryption_scheme_t | encryption_scheme, | ||
| const uint8_t * | encrypted_message, | ||
| uint16_t | encrypted_message_length, | ||
| const uint8_t * | label, | ||
| uint16_t | label_length, | ||
| optiga_key_id_t | private_key, | ||
| uint8_t * | message, | ||
| uint16_t * | message_length | ||
| ) |
Decrypts input data using OPTIGA private key and export it to the host.
Decrypts input data using RSA private key from OPTIGA and exports the decrypted data to the host.
| [in] | me | Valid instance of optiga_crypt_t created using optiga_crypt_create. |
| [in] | encryption_scheme | RSA encryption scheme. |
| [in] | encrypted_message | Pointer to the data to be decrypted. |
| [in] | encrypted_message_length | Length of the data to be decrypted. |
| [in] | label | Pointer to a label (Reserved for future use). |
| [in] | label_length | Length of the label (Reserved for future use). |
| [in] | private_key | RSA private key in OPTIGA |
| [in,out] | message | Pointer to buffer to store decrypted message. |
| [in,out] | message_length | Pointer to length of the decrypted message. |
| OPTIGA_CRYPT_SUCCESS | Successful invocation |
| OPTIGA_CRYPT_ERROR_INVALID_INPUT | Wrong Input arguments provided |
| OPTIGA_CRYPT_ERROR_INSTANCE_IN_USE | The previous operation with the same instance is not complete |
| OPTIGA_DEVICE_ERROR | Command execution failure in OPTIGA and the LSB indicates the error code. (Refer Solution Reference Manual) |
Example
example_optiga_crypt_decrypt.c
| optiga_lib_status_t optiga_crypt_rsa_decrypt_and_store | ( | optiga_crypt_t * | me, |
| optiga_rsa_encryption_scheme_t | encryption_scheme, | ||
| const uint8_t * | encrypted_message, | ||
| uint16_t | encrypted_message_length, | ||
| const uint8_t * | label, | ||
| uint16_t | label_length, | ||
| optiga_key_id_t | private_key | ||
| ) |
Decrypts input data using OPTIGA private key and stores it in a OPTIGA session.
Decrypts input data using RSA private key from OPTIGA and stores it in a OPTIGA session.
| [in] | me | Valid instance of optiga_crypt_t created using optiga_crypt_create. |
| [in] | encryption_scheme | RSA encryption scheme. |
| [in] | encrypted_message | Pointer to the data to be decrypted. |
| [in] | encrypted_message_length | Length of the data to be decrypted. |
| [in] | label | Pointer to a label (Reserved for future use). |
| [in] | label_length | Length of the label (Reserved for future use). |
| [in] | private_key | RSA private key in OPTIGA. |
| OPTIGA_CRYPT_SUCCESS | Successful invocation |
| OPTIGA_CRYPT_ERROR_INVALID_INPUT | Wrong Input arguments provided |
| OPTIGA_CRYPT_ERROR_INSTANCE_IN_USE | The previous operation with the same instance is not complete |
| OPTIGA_DEVICE_ERROR | Command execution failure in OPTIGA and the LSB indicates the error code. (Refer Solution Reference Manual) |
Example
example_optiga_crypt_decrypt.c
| _STATIC_H optiga_lib_status_t optiga_crypt_rsa_enc_dec | ( | optiga_crypt_t * | me, |
| optiga_rsa_encryption_scheme_t | encryption_scheme, | ||
| const uint8_t * | p_message, | ||
| uint16_t | message_length, | ||
| const uint8_t * | p_label, | ||
| uint16_t | label_length, | ||
| uint8_t | public_key_source_type, | ||
| const void * | p_key, | ||
| uint8_t * | p_processed_message, | ||
| uint16_t * | p_processed_message_length, | ||
| bool_t | is_enc | ||
| ) |
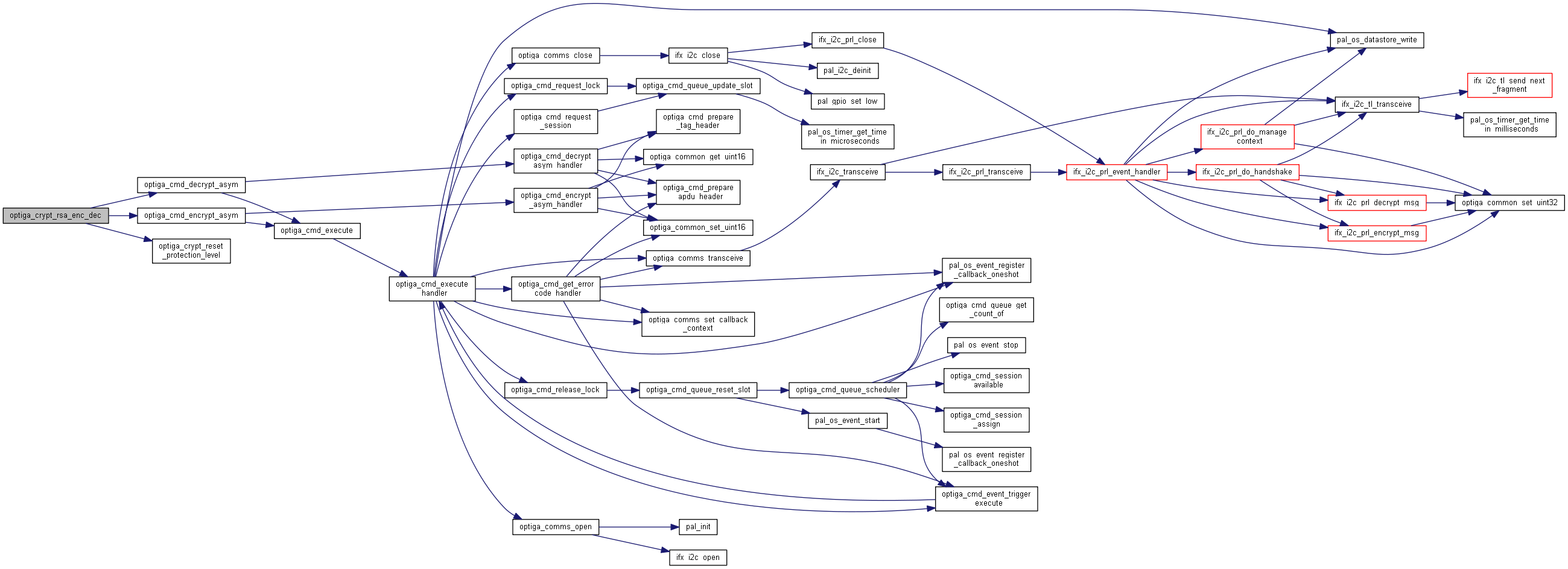
| optiga_lib_status_t optiga_crypt_rsa_encrypt_message | ( | optiga_crypt_t * | me, |
| optiga_rsa_encryption_scheme_t | encryption_scheme, | ||
| const uint8_t * | message, | ||
| uint16_t | message_length, | ||
| const uint8_t * | label, | ||
| uint16_t | label_length, | ||
| uint8_t | public_key_source_type, | ||
| const void * | public_key, | ||
| uint8_t * | encrypted_message, | ||
| uint16_t * | encrypted_message_length | ||
| ) |
Encrypts message using RSA public key.
Encrypts message using RSA public key which is either provided by the host or stored in OPTIGA.
| [in] | me | Valid instance of optiga_crypt_t created using optiga_crypt_create. |
| [in] | encryption_scheme | RSA encryption scheme. |
| [in] | message | Pointer to message to be encrypted. |
| [in] | message_length | Length of the message to be encrypted. |
| [in] | label | Pointer to a label (Reserved for future use). |
| [in] | label_length | Length of the label (Reserved for future use). |
| [in] | public_key_source_type | Public key from host / public key of certificate OID from OPTIGA. Value must be one of the below
|
| [in] | public_key | Public key from host / public key of certificate OID. Value must be one of the below
|
| [in,out] | encrypted_message | Pointer to buffer to store encrypted message. |
| [in,out] | encrypted_message_length | Pointer to length of the encrypted message. |
| OPTIGA_CRYPT_SUCCESS | Successful invocation |
| OPTIGA_CRYPT_ERROR_INVALID_INPUT | Wrong Input arguments provided |
| OPTIGA_CRYPT_ERROR_INSTANCE_IN_USE | The previous operation with the same instance is not complete |
| OPTIGA_DEVICE_ERROR | Command execution failure in OPTIGA and the LSB indicates the error code. (Refer Solution Reference Manual) |
Example
example_optiga_crypt_encrypt_message.c
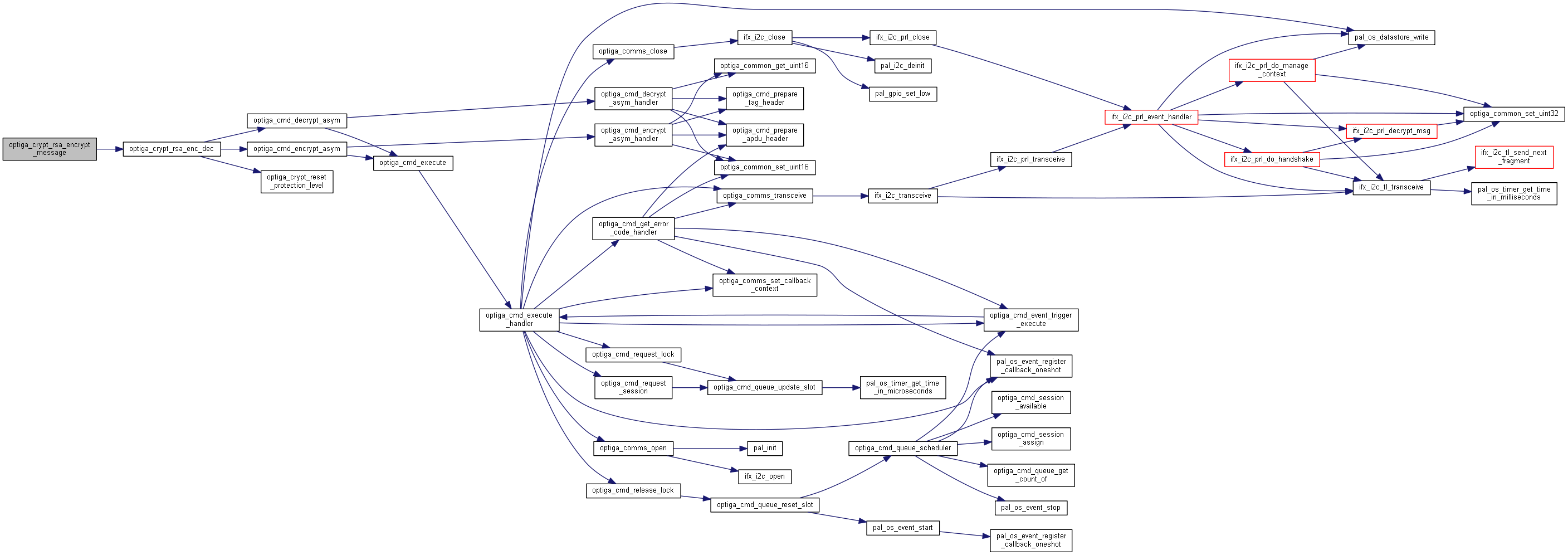
| optiga_lib_status_t optiga_crypt_rsa_encrypt_session | ( | optiga_crypt_t * | me, |
| optiga_rsa_encryption_scheme_t | encryption_scheme, | ||
| const uint8_t * | label, | ||
| uint16_t | label_length, | ||
| uint8_t | public_key_source_type, | ||
| const void * | public_key, | ||
| uint8_t * | encrypted_message, | ||
| uint16_t * | encrypted_message_length | ||
| ) |
Encrypts session data using RSA public key.
Encrypts session data using RSA public key which is either provided by the host or stored in OPTIGA.
| [in] | me | Valid instance of optiga_crypt_t created using optiga_crypt_create. |
| [in] | encryption_scheme | RSA encryption scheme. |
| [in] | label | Pointer to a label (used only is case of RSAES_OAEP_SHA256 otherwise ignored). |
| [in] | label_length | Length of the label (used only is case of RSAES_OAEP_SHA256 otherwise ignored). |
| [in] | public_key_source_type | Public key from host / public key of certificate OID from OPTIGA. Value must be one of the below
|
| [in] | public_key | Public key from host / public key of certificate OID. Value must be one of the below
|
| [in,out] | encrypted_message | Pointer to buffer to store encrypted message. |
| [in,out] | encrypted_message_length | Pointer to length of the encrypted message. |
| OPTIGA_CRYPT_SUCCESS | Successful invocation |
| OPTIGA_CRYPT_ERROR_INVALID_INPUT | Wrong Input arguments provided |
| OPTIGA_CRYPT_ERROR_INSTANCE_IN_USE | The previous operation with the same instance is not complete |
| OPTIGA_DEVICE_ERROR | Command execution failure in OPTIGA and the LSB indicates the error code. (Refer Solution Reference Manual) |
Example
example_optiga_crypt_encrypt_session.c
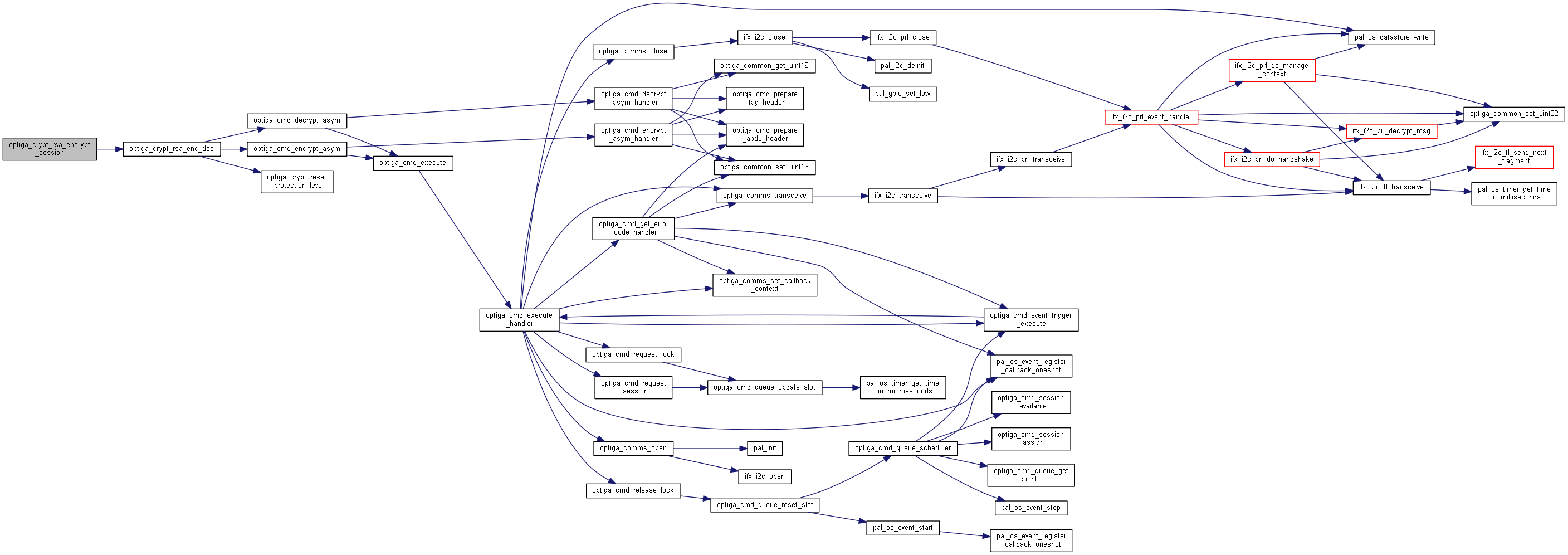
| optiga_lib_status_t optiga_crypt_rsa_generate_keypair | ( | optiga_crypt_t * | me, |
| optiga_rsa_key_type_t | key_type, | ||
| uint8_t | key_usage, | ||
| bool_t | export_private_key, | ||
| void * | private_key, | ||
| uint8_t * | public_key, | ||
| uint16_t * | public_key_length | ||
| ) |
Generates an key pair based on RSA key type.
Generates an RSA key-pair based on the type of the key.
| [in] | me | Valid instance of optiga_crypt_t created using optiga_crypt_create. |
| [in] | key_type | RSA key type defined by optiga_rsa_key_type_t. |
| [in] | key_usage | Key usage defined by optiga_key_usage_t.
|
| [in] | export_private_key | TRUE (1) or a non-zero value - Exports private key to the host. FALSE (0) - Exports only public key to the host and writes private key to OPTIGA. The input key_usage is ignored. |
| [in,out] | private_key | Buffer to store private key or private key OID of OPTIGA, must not be NULL.
|
| [in,out] | public_key | Buffer to store public key, must not be NULL. |
| [in,out] | public_key_length | Initially set as length of public_key, later updated as actual length of public_key. |
| OPTIGA_CRYPT_SUCCESS | Successful invocation |
| OPTIGA_CRYPT_ERROR_INVALID_INPUT | Wrong Input arguments provided |
| OPTIGA_CRYPT_ERROR_INSTANCE_IN_USE | The previous operation with the same instance is not complete |
| OPTIGA_DEVICE_ERROR | Command execution failure in OPTIGA and the LSB indicates the error code. (Refer Solution Reference Manual) |
Example
example_optiga_crypt_rsa_generate_keypair.c
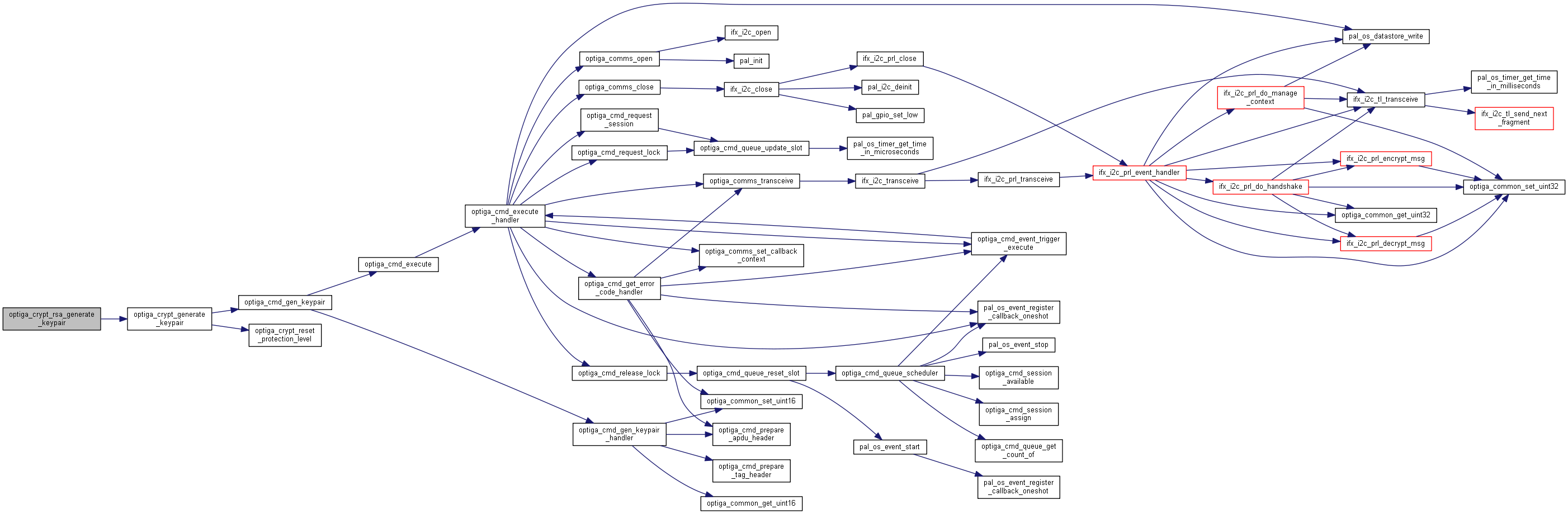
| optiga_lib_status_t optiga_crypt_rsa_generate_pre_master_secret | ( | optiga_crypt_t * | me, |
| const uint8_t * | optional_data, | ||
| uint16_t | optional_data_length, | ||
| uint16_t | pre_master_secret_length | ||
| ) |
Generates a pre-master secret.
Generates a pre-master secret for RSA key exchange and stores in the acquired session
| [in] | me | Valid instance of optiga_crypt_t created using optiga_crypt_create. |
| [in] | optional_data | Optional data that gets prepended to the generated random secret.
|
| [in] | optional_data_length | Length of the optional data provided. It is ignored if optional_data is NULL
|
| [in] | pre_master_secret_length | Length of the shared secret to be generated.
|
| OPTIGA_CRYPT_SUCCESS | Successful invocation. |
| OPTIGA_CRYPT_ERROR_INVALID_INPUT | Wrong Input arguments provided.
|
| OPTIGA_CRYPT_ERROR_INSTANCE_IN_USE | The previous operation with the same instance is not complete. |
| OPTIGA_DEVICE_ERROR | Command execution failure in OPTIGA and the LSB indicates the error code. (Refer Solution Reference Manual) |
Example
example_optiga_crypt_encrypt_session.c
Maximum length of shared secret supported by OPTIGA is 48 bytes, minimum is 8 bytes.
The minimum difference between shared secret length and optional data length should be 8 bytes, since the minimum random length OPTIGA expects is 8 bytes (optional_data_length <= shared_length � 8 bytes).
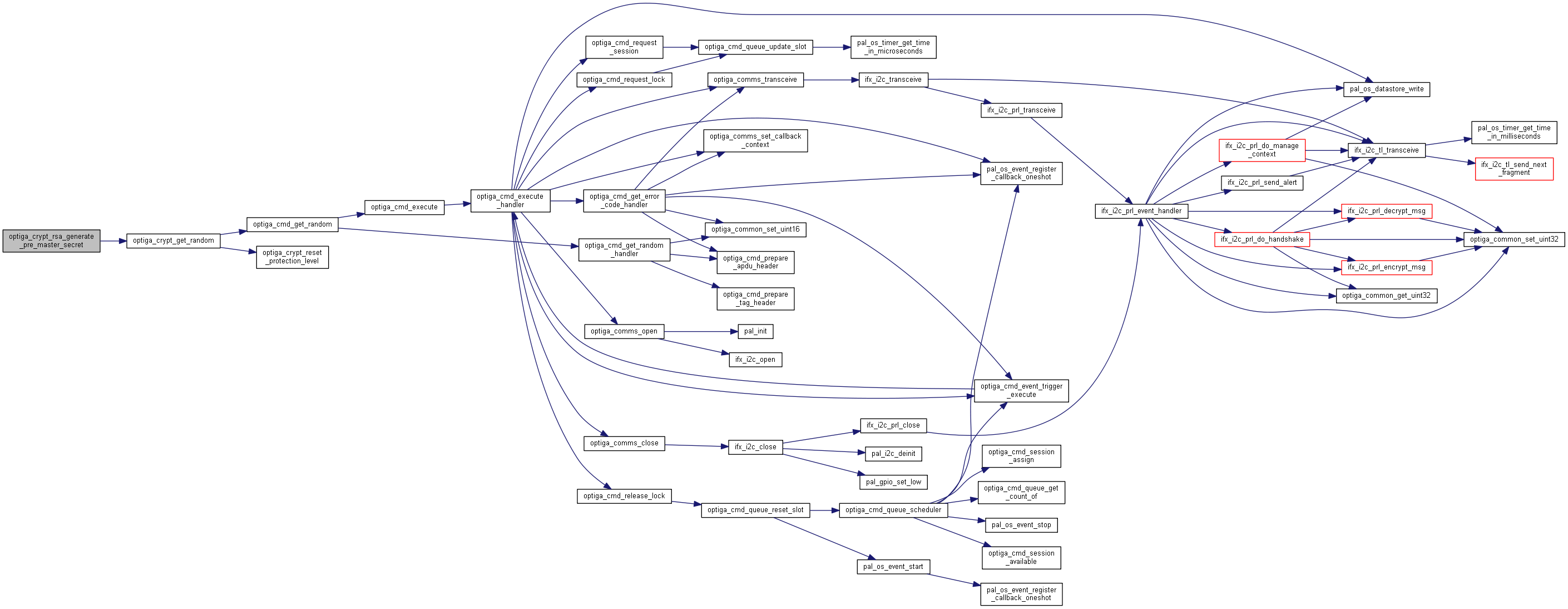
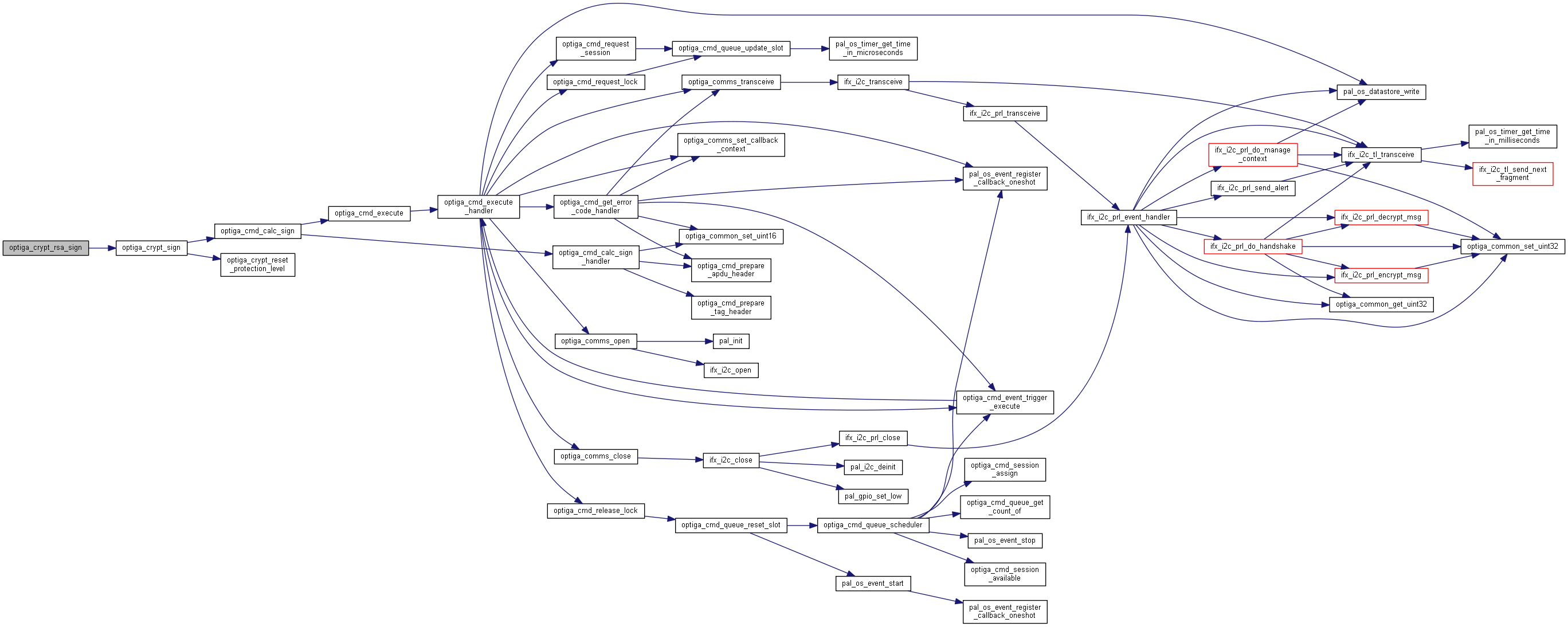
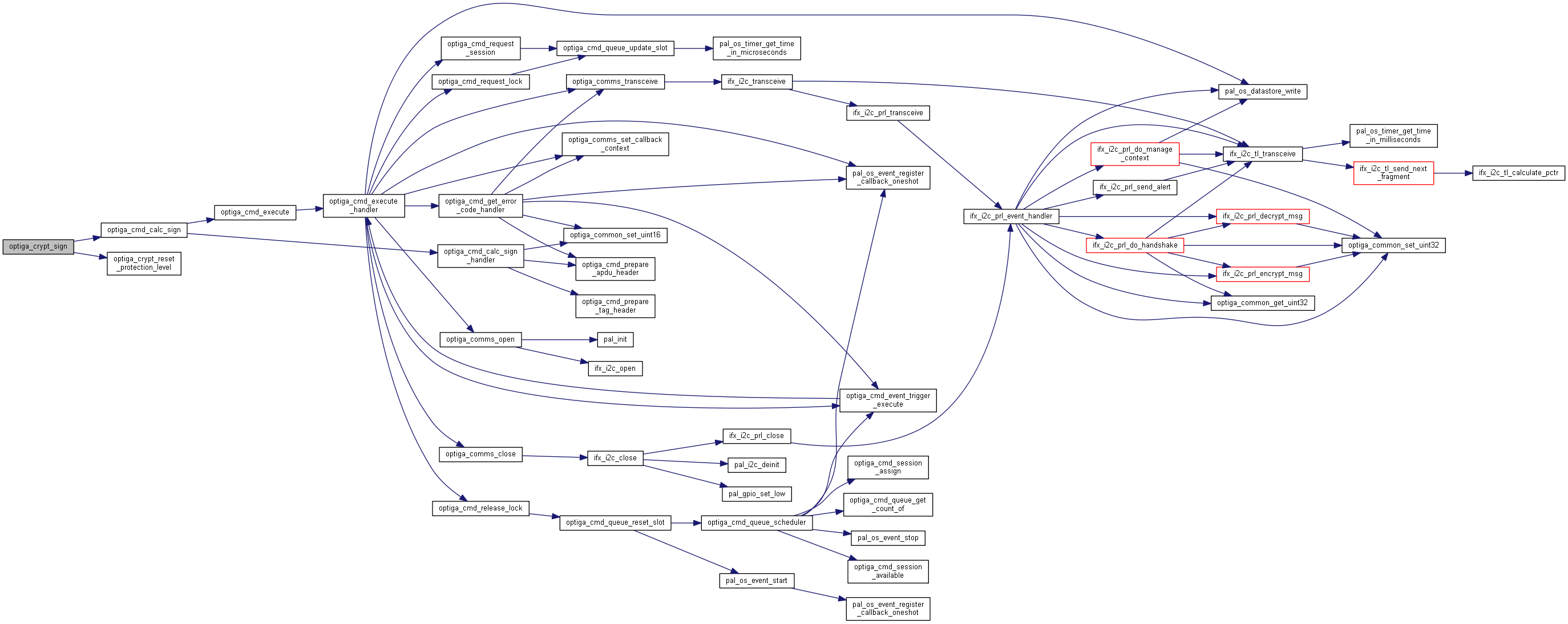
| optiga_lib_status_t optiga_crypt_rsa_sign | ( | optiga_crypt_t * | me, |
| optiga_rsa_signature_scheme_t | signature_scheme, | ||
| const uint8_t * | digest, | ||
| uint8_t | digest_length, | ||
| optiga_key_id_t | private_key, | ||
| uint8_t * | signature, | ||
| uint16_t * | signature_length, | ||
| uint16_t | salt_length | ||
| ) |
Generates a RSA signature for the given digest based on the input signature scheme.
Generates a signature for the given digest using private key stored in OPTIGA.
| [in] | me | Valid instance of optiga_crypt_t created using optiga_crypt_create. |
| [in] | signature_scheme | RSA signature scheme defined by optiga_rsa_signature_scheme_t |
| [in] | digest | Digest on which signature is generated. |
| [in] | digest_length | Length of the input digest. |
| [in] | private_key | Private key OID to generate signature. This is static private key only. |
| [in,out] | signature | Pointer to store generated signature, must not be NULL. |
| [in] | signature_length | Length of signature. Initial value set as length of buffer, later updated as the actual length of generated signature.
|
| [in] | salt_length | Reserved for future use. Parameter for RSA PSS signature scheme. |
| OPTIGA_CRYPT_SUCCESS | Successful invocation. |
| OPTIGA_CRYPT_ERROR_INVALID_INPUT | Wrong Input arguments provided. |
| OPTIGA_CRYPT_ERROR_INSTANCE_IN_USE | The previous operation with the same instance is not complete. |
| OPTIGA_DEVICE_ERROR | Command execution failure in OPTIGA and the LSB indicates the error code. (Refer Solution Reference Manual) |
Example
example_optiga_crypt_rsa_sign.c
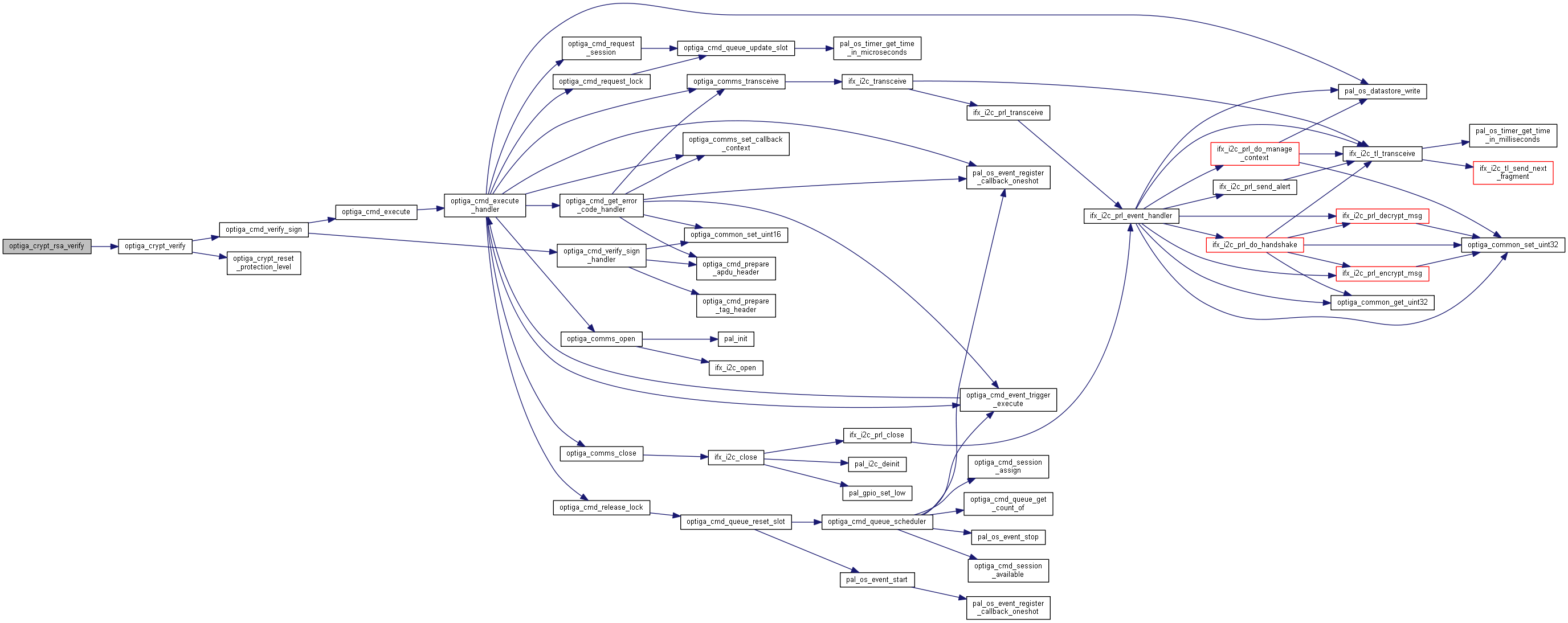
| optiga_lib_status_t optiga_crypt_rsa_verify | ( | optiga_crypt_t * | me, |
| optiga_rsa_signature_scheme_t | signature_scheme, | ||
| const uint8_t * | digest, | ||
| uint8_t | digest_length, | ||
| const uint8_t * | signature, | ||
| uint16_t | signature_length, | ||
| uint8_t | public_key_source_type, | ||
| const void * | public_key, | ||
| uint16_t | salt_length | ||
| ) |
Verifies the RSA signature over the given digest.
Verifies the signature over a given digest provided with the input data.
| [in] | me | Valid instance of optiga_crypt_t created using optiga_crypt_create. |
| [in] | signature_scheme | RSA signature scheme defined by optiga_rsa_signature_scheme_t |
| [in] | digest | Pointer to a given digest buffer, must not be NULL. |
| [in] | digest_length | Length of digest. |
| [in] | signature | Pointer to a given signature buffer, must not be NULL. |
| [in] | signature_length | Length of signature. |
| [in] | public_key_source_type | Public key from host / public key of certificate OID from OPTIGA. Value must be one of the below
|
| [in] | public_key | Public key from host / public key of certificate OID. Value must be one of the below
|
| [in] | salt_length | Reserved for future use. Parameter for RSA PSS signature scheme. |
| OPTIGA_CRYPT_SUCCESS | Successful invocation |
| OPTIGA_CRYPT_ERROR_INVALID_INPUT | Wrong Input arguments provided |
| OPTIGA_CRYPT_ERROR_INSTANCE_IN_USE | The previous operation with the same instance is not complete |
| OPTIGA_DEVICE_ERROR | Command execution failure in OPTIGA and the LSB indicates the error code. (Refer Solution Reference Manual) |
Example
example_optiga_crypt_rsa_verify.c
| void optiga_crypt_set_comms_params | ( | optiga_crypt_t * | me, |
| uint8_t | configuration_type, | ||
| uint8_t | value | ||
| ) |
Sets/updates the OPTIGA Comms Shielded connection configuration in the respective (optiga_util) instance.
Sets/updates the OPTIGA Comms Shielded connection configuration in the respective (optiga_util) instance.
| [in,out] | me | Valid instance of optiga_util_t |
| [in] | configuration_type | Configuration Type Possible Types are OPTIGA_COMMS_PROTECTION_LEVEL OPTIGA_COMMS_PROTOCOL_VERSION |
| [in] | value | Value part for the respective configuration |
Example
| _STATIC_H optiga_lib_status_t optiga_crypt_sign | ( | optiga_crypt_t * | me, |
| uint8_t | signature_scheme, | ||
| const uint8_t * | p_digest, | ||
| uint8_t | digest_length, | ||
| optiga_key_id_t | private_key, | ||
| uint8_t * | p_signature, | ||
| uint16_t * | p_signature_length, | ||
| uint16_t | salt_length | ||
| ) |
| optiga_lib_status_t optiga_crypt_tls_prf_sha256 | ( | optiga_crypt_t * | me, |
| uint16_t | secret, | ||
| const uint8_t * | label, | ||
| uint16_t | label_length, | ||
| const uint8_t * | seed, | ||
| uint16_t | seed_length, | ||
| uint16_t | derived_key_length, | ||
| bool_t | export_to_host, | ||
| uint8_t * | derived_key | ||
| ) |
Derives a key.
Derives a key using the secret stored in OPTIGA.
| [in] | me | Valid instance of optiga_crypt_t created using optiga_crypt_create. |
| [in] | secret | Object ID of the secret stored in OPTIGA.
|
| [in] | label | Pointer to the label, can be NULL if not applicable. |
| [in] | label_length | Length of the label. |
| [in] | seed | Valid pointer to the seed, must not be NULL. |
| [in] | seed_length | Length of the seed. |
| [in] | derived_key_length | Length of derived key. |
| [in] | export_to_host | TRUE (1) or Non-Zero value - Exports the derived key to Host. FALSE (0) - Stores the derived key into the session object ID acquired by the instance. |
| [in,out] | derived_key | Pointer to the valid buffer with a minimum size of derived_key_length, in case of exporting the key to host(export_to_host is non-zero value). Otherwise set to NULL. |
| OPTIGA_CRYPT_SUCCESS | Successful invocation |
| OPTIGA_CRYPT_ERROR_INVALID_INPUT | Wrong Input arguments provided |
| OPTIGA_CRYPT_ERROR_INSTANCE_IN_USE | The previous operation with the same instance is not complete |
| OPTIGA_DEVICE_ERROR | Command execution failure in OPTIGA and the LSB indicates the error code. (Refer Solution Reference Manual) |
Example
example_optiga_crypt_tls_prf_sha256.c
| _STATIC_H optiga_lib_status_t optiga_crypt_verify | ( | optiga_crypt_t * | me, |
| uint8_t | cmd_param, | ||
| const uint8_t * | p_digest, | ||
| uint8_t | digest_length, | ||
| const uint8_t * | p_signature, | ||
| uint16_t | signature_length, | ||
| uint8_t | public_key_source_type, | ||
| const void * | p_public_key, | ||
| uint16_t | salt_length | ||
| ) |