#include <OPTIGATrustM.h>
Public Member Functions | |
| IFX_OPTIGA_TrustM () | |
| ~IFX_OPTIGA_TrustM () | |
| int32_t | begin (uint8_t pairDevice=1) |
| int32_t | begin (TwoWire &CustomWire) |
| int32_t | checkChip (void) |
| int32_t | pairMCU (void) |
| int32_t | reset (void) |
| void | end (void) |
| Ends communication with the Optiga Trust M. More... | |
| int32_t | getCertificate (uint8_t certificate[], uint16_t &certificateLength) |
| Get the Infineon OPTIGA Trust M device certificate. More... | |
| int32_t | getPublicKey (uint8_t publickey[68]) |
| Get the Infineon OPTIGA Trust M device certificate public key. More... | |
| int32_t | getUniqueID (uint8_t uniqueID[], uint16_t &uidLength) |
| int32_t | getRandom (uint16_t length, uint8_t random[]) |
| Get a random number. More... | |
| int32_t | getCurrentLimit (uint8_t ¤tLim) |
| int32_t | setCurrentLimit (uint8_t currentLim) |
| int32_t | getLastErrorCodes (uint8_t errorCodes[], uint16_t &errorCodesLength) |
| int32_t | sha256 (uint8_t dataToHash[], uint16_t dlen, uint8_t hash[32]) |
| int32_t | calculateSignature (uint8_t dataToSign[], uint16_t dlen, uint16_t privateKey_oid, uint8_t result[], uint16_t &rlen) |
| int32_t | calculateSignature (uint8_t dataToSign[], uint16_t dlen, uint8_t result[], uint16_t &rlen) |
| int32_t | calculateSignatureRSA (uint8_t dataToSign[], uint16_t dlen, uint16_t privateKey_oid, uint8_t result[], uint16_t &rlen) |
| int32_t | calculateSignatureRSA (uint8_t dataToSign[], uint16_t dlen, uint8_t result[], uint16_t &rlen) |
| int32_t | calculateSignatureECDSA (uint8_t dataToSign[], uint16_t dlen, uint16_t privateKey_oid, uint8_t result[], uint16_t &rlen) |
| int32_t | calculateSignatureECDSA (uint8_t dataToSign[], uint16_t dlen, uint8_t result[], uint16_t &rlen) |
| int32_t | formatSignature (uint8_t signature[], uint16_t signatureLength, uint8_t result[], uint16_t &rlen) |
| int32_t | verifySignature (uint8_t hash[], uint16_t hashLength, uint8_t signature[], uint16_t signatureLength, uint16_t publicKey_oid) |
| int32_t | verifySignature (uint8_t hash[], uint16_t hashLength, uint8_t signature[], uint16_t signatureLength) |
| int32_t | verifySignature (uint8_t hash[], uint16_t hashLength, uint8_t signature[], uint16_t signatureLength, uint8_t pubKey[], uint16_t plen) |
| int32_t | verifySignatureRSA (uint8_t hash[], uint16_t hashLength, uint8_t signature[], uint16_t signatureLength, uint16_t publicKey_oid) |
| int32_t | verifySignatureRSA (uint8_t hash[], uint16_t hashLength, uint8_t signature[], uint16_t signatureLength, uint8_t pubKey[], uint16_t plen, optiga_rsa_key_type rsa_key_type) |
| int32_t | verifySignatureECDSA (uint8_t hash[], uint16_t hashLength, uint8_t signature[], uint16_t signatureLength, uint16_t publicKey_oid) |
| int32_t | verifySignatureECDSA (uint8_t hash[], uint16_t hashLength, uint8_t signature[], uint16_t signatureLength, uint8_t pubKey[], uint16_t plen, optiga_ecc_curve_t ecc_key_type) |
| int32_t | sharedSecret (uint8_t publicKey[], uint16_t plen) |
| int32_t | sharedSecret (uint16_t oid, uint8_t publicKey[], uint16_t plen) |
| int32_t | sharedSecret (String curveName, uint8_t publicKey[], uint16_t plen) |
| int32_t | sharedSecret (String curveName, uint16_t oid, uint8_t publicKey[], uint16_t plen) |
| int32_t | sharedSecretWithExport (uint8_t publicKey[], uint16_t plen, uint8_t sharedSecret[], uint16_t &shlen) |
| int32_t | sharedSecretWithExport (String curveName, uint8_t publicKey[], uint16_t plen, uint8_t sharedSecret[], uint16_t &shlen) |
| int32_t | generateKeypair (uint8_t publicKey[], uint16_t &plen) |
| int32_t | generateKeypair (uint8_t publicKey[], uint16_t &plen, uint16_t privateKey_oid) |
| int32_t | generateKeypair (uint8_t publicKey[], uint16_t &plen, uint8_t privateKey[], uint16_t &prlen) |
| int32_t | generateKeypairRSA (uint8_t publicKey[], uint16_t &plen) |
| int32_t | generateKeypairRSA (uint8_t *p_pubkey, uint16_t &plen, uint16_t privateKey_oid, optiga_rsa_key_type_t rsa_key_type) |
| int32_t | generateKeypairRSA (uint8_t *p_pubkey, uint16_t &plen, uint8_t *p_privkey, uint16_t &prlen, optiga_rsa_key_type_t rsa_key_type) |
| int32_t | generateKeypairRSA1024 (uint8_t *p_pubkey, uint16_t &plen, uint8_t *p_privkey, uint16_t &prlen) |
| int32_t | generateKeypairRSA1024 (uint8_t *p_pubkey, uint16_t &plen, uint16_t privateKey_oid) |
| int32_t | generateKeypairRSA2048 (uint8_t *p_pubkey, uint16_t &plen, uint8_t *p_privkey, uint16_t &prlen) |
| int32_t | generateKeypairRSA2048 (uint8_t *p_pubkey, uint16_t &plen, uint16_t privateKey_oid) |
| int32_t | generateKeypairECC (uint8_t publicKey[], uint16_t &plen) |
| int32_t | generateKeypairECC (uint8_t *p_pubkey, uint16_t &plen, uint16_t privateKey_oid, optiga_ecc_curve_t ecc_key_type) |
| int32_t | generateKeypairECC (uint8_t *p_pubkey, uint16_t &plen, uint8_t *p_privkey, uint16_t &prlen, optiga_ecc_curve_t ecc_key_type) |
| int32_t | generateKeypairECCP256 (uint8_t *p_pubkey, uint16_t &plen, uint8_t *p_privkey, uint16_t &prlen) |
| int32_t | generateKeypairECCP256 (uint8_t *p_pubkey, uint16_t &plen, uint16_t privateKey_oid) |
| int32_t | generateKeypairECCP384 (uint8_t *p_pubkey, uint16_t &plen, uint8_t *p_privkey, uint16_t &prlen) |
| int32_t | generateKeypairECCP384 (uint8_t *p_pubkey, uint16_t &plen, uint16_t privateKey_oid) |
| int32_t | encrypt (uint8_t dataToEncrypt[], uint16_t dlen, uint8_t pubkeyFromUser[], uint16_t pklen, uint8_t result[], uint16_t &rlen) |
| int32_t | encrypt (uint8_t dataToEncrypt[], uint16_t dlen, uint16_t certOID, uint8_t result[], uint16_t &rlen) |
| int32_t | decrypt (uint8_t dataToDecrypt[], uint16_t dlen, uint16_t keyOID, uint8_t result[], uint16_t &rlen) |
| IFX_OPTIGA_TrustM::IFX_OPTIGA_TrustM | ( | ) |
| IFX_OPTIGA_TrustM::~IFX_OPTIGA_TrustM | ( | ) |
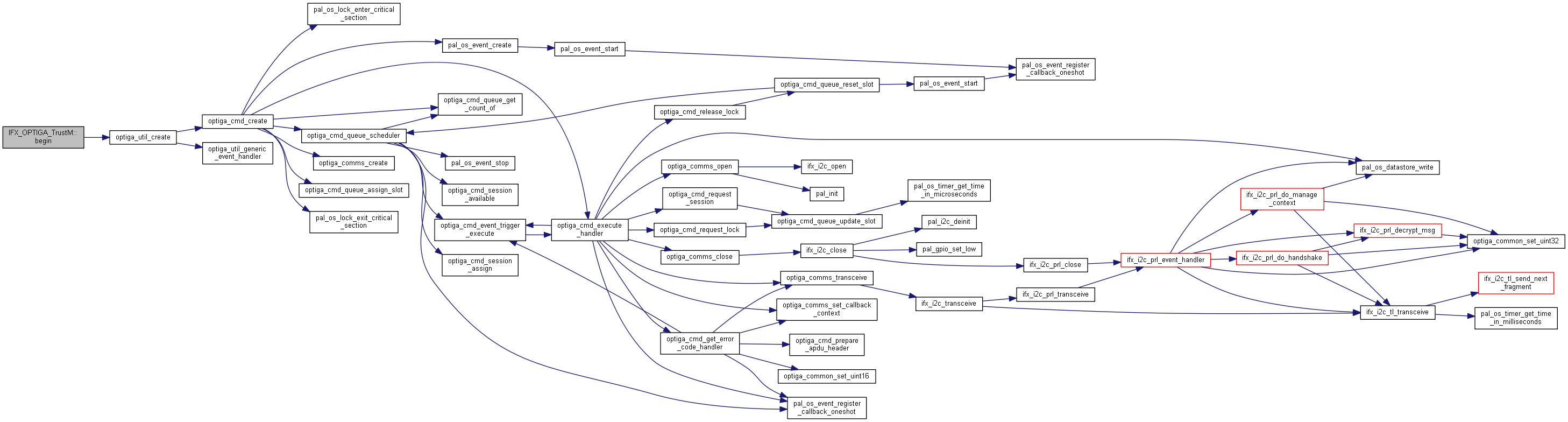
| int32_t IFX_OPTIGA_TrustM::begin | ( | uint8_t | pairDevice = 1 | ) |
This function initializes the Infineon OPTIGA Trust X command library and sends the 'open application' command to the device. This opens the communicatino channel to the Optiga Trust M, so that you can carry out different operations
| [in] | pairDevice | Define whether you want to pair MCU and OPTIGA Trust M devices. |
| 0 | If function was successful. |
| 1 | If the operation failed. |
Create OPTIGA Crypt Instance
Open the application on OPTIGA which is a precondition to perform any other operations using optiga_util_open_application
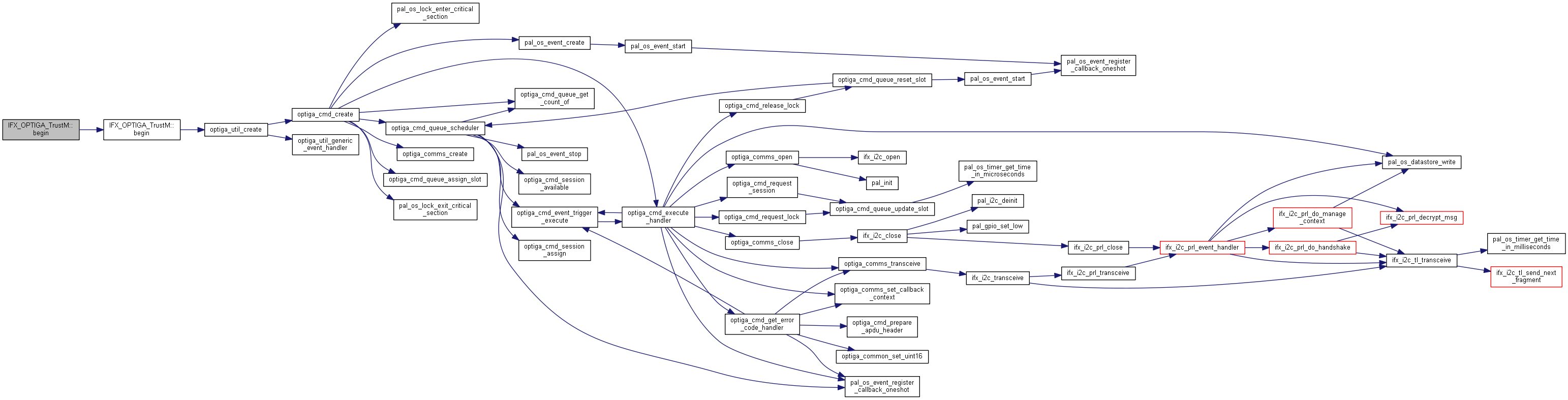
| int32_t IFX_OPTIGA_TrustM::begin | ( | TwoWire & | CustomWire | ) |
This function initializes the Infineon OPTIGA Trust M command library and sends the 'open application' command to the device. This opens the communicatino channel to the Optiga Trust M, so that you can carry out different operations
| [in] | CustomWire | Reference to a custom TwoWire object used with the Optiga. |
| 0 | If function was successful. |
| 1 | If the operation failed. |
Set the corresponding i2c context first
|
inline |
This function generates an ECDSA signature.
| [in] | dataToSign | Pointer to the data |
| [in] | dlen | Length of the input data |
| [in] | privateKey_oid | [Optional] Object ID defines which private key slot will be used to generate the signature. Default is the first slot. Use either one of: eDEVICE_PRIKEY_1 (Default) eDEVICE_PRIKEY_2 eDEVICE_PRIKEY_3 eDEVICE_PRIKEY_4 slots define below or eSessionCtxId_d session contexts |
| [out] | result | Pointer to the data array where the final result should be stored. |
| [out] | rlen | Length of the output data. Will be modified in case of success. |
| 0 | If function was successful. |
| 1 | If the operation failed. |
|
inline |
| int32_t IFX_OPTIGA_TrustM::calculateSignatureECDSA | ( | uint8_t | dataToSign[], |
| uint16_t | dlen, | ||
| uint16_t | privateKey_oid, | ||
| uint8_t | result[], | ||
| uint16_t & | rlen | ||
| ) |
This function generates an ECDSA signature.
| [in] | dataToSign | Pointer to the data |
| [in] | dlen | Length of the input data |
| [in] | privateKey_oid | [Optional] Object ID defines which private key slot will be used to generate the signature. Default is the first slot. Use either one of: eDEVICE_PRIKEY_1 (Default) eDEVICE_PRIKEY_2 eDEVICE_PRIKEY_3 eDEVICE_PRIKEY_4 slots define below or eSessionCtxId_d session contexts |
| [out] | result | Pointer to the data array where the final result should be stored. |
| [out] | rlen | Length of the output data. Will be modified in case of success. |
| 0 | If function was successful. |
| 1 | If the operation failed. |
|
inline |
| int32_t IFX_OPTIGA_TrustM::calculateSignatureRSA | ( | uint8_t | dataToSign[], |
| uint16_t | dlen, | ||
| uint16_t | privateKey_oid, | ||
| uint8_t | result[], | ||
| uint16_t & | rlen | ||
| ) |
This function generates an RSA signature.
| [in] | dataToSign | Pointer to the data |
| [in] | dlen | Length of the input data |
| [in] | privateKey_oid | [Optional] Object ID defines which private key slot will be used to generate the signature. Default is the first slot. Use either one of: eDEVICE_PRIKEY_1 (Default) eDEVICE_PRIKEY_2 eDEVICE_PRIKEY_3 eDEVICE_PRIKEY_4 slots define below or eSessionCtxId_d session contexts |
| [out] | result | Pointer to the data array where the final result should be stored. |
| [out] | rlen | Length of the output data. Will be modified in case of success. |
| 0 | If function was successful. |
| 1 | If the operation failed. |
|
inline |
| int32_t IFX_OPTIGA_TrustM::checkChip | ( | void | ) |
This function checks whether the chip posseses the genuine certificate
| 0 | If function was successful. |
| 1 | If the operation failed. |
| int32_t IFX_OPTIGA_TrustM::decrypt | ( | uint8_t | dataToDecrypt[], |
| uint16_t | dlen, | ||
| uint16_t | keyOID, | ||
| uint8_t | result[], | ||
| uint16_t & | rlen | ||
| ) |
This function decrypt user given data with RSAES PKCS1 v1.5 Scheme.
| [in] | dataToDecrypt | Pointer to the data |
| [in] | dlen | Length of the input data |
| [in] | keyOID | Object ID defines which key will be used to decrypt the message. Default is the first slot. Use either one of: eRSA_DEVICE_PRIKEY_1 (Default) eRSA_DEVICE_PRIKEY_2 |
| [out] | result | Pointer to the data array where the final result should be stored. |
| [out] | rlen | Length of the output data. Will be modified in case of success. |
| 0 | If function was successful. |
| 1 | If the operation failed. |
| int32_t IFX_OPTIGA_TrustM::encrypt | ( | uint8_t | dataToEncrypt[], |
| uint16_t | dlen, | ||
| uint8_t | pubkeyFromUser[], | ||
| uint16_t | pklen, | ||
| uint8_t | result[], | ||
| uint16_t & | rlen | ||
| ) |
This function encrypt user given data with RSAES PKCS1 v1.5 Scheme.
| [in] | dataToEncrypt | Pointer to the data |
| [in] | dlen | Length of the input data |
| [in] | pubkeyFromUser | A user provided RSA public key. |
| [in] | pklen | Public key length |
| [out] | result | Pointer to the data array where the final result should be stored. |
| [out] | rlen | Length of the output data. Will be modified in case of success. |
| 0 | If function was successful. |
| 1 | If the operation failed. |
| int32_t IFX_OPTIGA_TrustM::encrypt | ( | uint8_t | dataToEncrypt[], |
| uint16_t | dlen, | ||
| uint16_t | certOID, | ||
| uint8_t | result[], | ||
| uint16_t & | rlen | ||
| ) |
This function encrypt user given data with RSAES PKCS1 v1.5 Scheme.
| [in] | dataToEncrypt | Pointer to the data |
| [in] | dlen | Length of the input data |
| [in] | certOID | Object ID defines which public key will be used to encrypt the message (the public key will be extracted from the certificate). Default is the first slot. Use either one of: eDEVICE_PUBKEY_CERT_IFX (Default) eDEVICE_PUBKEY_CERT_PRJSPC_1 eDEVICE_PUBKEY_CERT_PRJSPC_2 eDEVICE_PUBKEY_CERT_PRJSPC_3 |
| [out] | result | Pointer to the data array where the final result should be stored. |
| [out] | rlen | Length of the output data. Will be modified in case of success. |
| 0 | If function was successful. |
| 1 | If the operation failed. |
| void IFX_OPTIGA_TrustM::end | ( | void | ) |
Ends communication with the Optiga Trust M.
| 0 | If function was successful. |
| 1 | If the operation failed. |
| int32_t IFX_OPTIGA_TrustM::formatSignature | ( | uint8_t | signature[], |
| uint16_t | signatureLength, | ||
| uint8_t | result[], | ||
| uint16_t & | rlen | ||
| ) |
This function encodes generated signature in ASN.1 format
| [in] | signature | Pointer to signature in DER format |
| [in] | signatureLength | Length of the input data |
| [out] | result | Pointer to the data array where the final result should be stored. |
| [out] | rlen | Length of the output data. Will be modified in case of success. |
| 0 | If function was successful. |
| 1 | If the operation failed. |
|
inline |
This function generates a RSA 1024 bits exponential public private keypair. You can store the private key internally or export it for your usage
| [out] | publicKey | Pointer to the data array where the result public key should be stored. |
| [out] | plen | Length of the public key |
| [in] | privateKey_oid | an Object ID of a slot, where the newly generated key should be stored: Use one of the following slots: eSESSION_ID_1 eSESSION_ID_2 (Default) eSESSION_ID_3 eSESSION_ID_4 eDEVICE_PRIKEY_1 eDEVICE_PRIKEY_2 eDEVICE_PRIKEY_3 eDEVICE_PRIKEY_4 |
| [out] | privateKey | [Optional] Pointer to the data array where the result private key should be stored. |
| [out] | prlen | [Optional] Length of the private key. |
| 0 | If function was successful. |
| 1 | If the operation failed. |
|
inline |
|
inline |
|
inline |
This function generates an ECC public private keypair. You can store the private key internally or export it for your usage
| [out] | publicKey | Pointer to the data array where the result public key should be stored. |
| [out] | plen | Length of the public key |
| [in] | privateKey_oid | an Object ID of a slot, where the newly generated key should be stored: Use one of the following slots: eSESSION_ID_1 eSESSION_ID_2 (Default) eSESSION_ID_3 eSESSION_ID_4 eDEVICE_PRIKEY_1 eDEVICE_PRIKEY_2 eDEVICE_PRIKEY_3 eDEVICE_PRIKEY_4 |
| [out] | privateKey | [Optional] Pointer to the data array where the result private key should be stored. |
| [out] | prlen | [Optional] Length of the private key. |
| [in] | ecc_key_type | [Optional] Public key ECC curve type |
| 0 | If function was successful. |
| 1 | If the operation failed. |
| int32_t IFX_OPTIGA_TrustM::generateKeypairECC | ( | uint8_t * | p_pubkey, |
| uint16_t & | plen, | ||
| uint16_t | privateKey_oid, | ||
| optiga_ecc_curve_t | ecc_key_type | ||
| ) |
Generate ECC Key pair
| int32_t IFX_OPTIGA_TrustM::generateKeypairECC | ( | uint8_t * | p_pubkey, |
| uint16_t & | plen, | ||
| uint8_t * | p_privkey, | ||
| uint16_t & | prlen, | ||
| optiga_ecc_curve_t | ecc_key_type | ||
| ) |
Generate ECC Key pair
|
inline |
This function generates an ECC NIST P 256 public private keypair. You can store the private key internally or export it for your usage
| [out] | publicKey | Pointer to the data array where the result public key should be stored. |
| [out] | plen | Length of the public key |
| [in] | privateKey_oid | an Object ID of a slot, where the newly generated key should be stored: Use one of the following slots: eSESSION_ID_1 eSESSION_ID_2 (Default) eSESSION_ID_3 eSESSION_ID_4 eDEVICE_PRIKEY_1 eDEVICE_PRIKEY_2 eDEVICE_PRIKEY_3 eDEVICE_PRIKEY_4 |
| [out] | privateKey | [Optional] Pointer to the data array where the result private key should be stored. |
| [out] | prlen | [Optional] Length of the private key. |
| 0 | If function was successful. |
| 1 | If the operation failed. |
|
inline |
|
inline |
This function generates an ECC NIST P 384 public private keypair. You can store the private key internally or export it for your usage
| [out] | publicKey | Pointer to the data array where the result public key should be stored. |
| [out] | plen | Length of the public key |
| [in] | privateKey_oid | an Object ID of a slot, where the newly generated key should be stored: Use one of the following slots: eSESSION_ID_1 eSESSION_ID_2 (Default) eSESSION_ID_3 eSESSION_ID_4 eDEVICE_PRIKEY_1 eDEVICE_PRIKEY_2 eDEVICE_PRIKEY_3 eDEVICE_PRIKEY_4 |
| [out] | privateKey | [Optional] Pointer to the data array where the result private key should be stored. |
| [out] | prlen | [Optional] Length of the private key. |
| 0 | If function was successful. |
| 1 | If the operation failed. |
|
inline |
|
inline |
This function generates a RSA type public private keypair. You can store the private key internally or export it for your usage
| [out] | publicKey | Pointer to the data array where the result public key should be stored. |
| [out] | plen | Length of the public key |
| [in] | privateKey_oid | an Object ID of a slot, where the newly generated key should be stored: Use one of the following slots: eSESSION_ID_1 eSESSION_ID_2 (Default) eSESSION_ID_3 eSESSION_ID_4 eDEVICE_PRIKEY_1 eDEVICE_PRIKEY_2 eDEVICE_PRIKEY_3 eDEVICE_PRIKEY_4 |
| [out] | privateKey | [Optional] Pointer to the data array where the result private key should be stored. |
| [out] | prlen | [Optional] Length of the private key. |
| [in] | rsa_key_type | [Optional] Public key RSA type |
| 0 | If function was successful. |
| 1 | If the operation failed. |
| int32_t IFX_OPTIGA_TrustM::generateKeypairRSA | ( | uint8_t * | p_pubkey, |
| uint16_t & | plen, | ||
| uint16_t | privateKey_oid, | ||
| optiga_rsa_key_type_t | rsa_key_type | ||
| ) |
Generate RSA Key pair
| int32_t IFX_OPTIGA_TrustM::generateKeypairRSA | ( | uint8_t * | p_pubkey, |
| uint16_t & | plen, | ||
| uint8_t * | p_privkey, | ||
| uint16_t & | prlen, | ||
| optiga_rsa_key_type_t | rsa_key_type | ||
| ) |
Generate RSA Key pair
|
inline |
This function generates RSA 1024 bits exponential type public private keypair. You can store the private key internally or export it for your usage
| [out] | publicKey | Pointer to the data array where the result public key should be stored. |
| [out] | plen | Length of the public key |
| [in] | privateKey_oid | an Object ID of a slot, where the newly generated key should be stored: Use one of the following slots: eSESSION_ID_1 eSESSION_ID_2 (Default) eSESSION_ID_3 eSESSION_ID_4 eDEVICE_PRIKEY_1 eDEVICE_PRIKEY_2 eDEVICE_PRIKEY_3 eDEVICE_PRIKEY_4 |
| [out] | privateKey | [Optional] Pointer to the data array where the result private key should be stored. |
| [out] | prlen | [Optional] Length of the private key. |
| 0 | If function was successful. |
| 1 | If the operation failed. |
|
inline |
|
inline |
This function generates RSA 2048 bits exponential type public private keypair. You can store the private key internally or export it for your usage
| [out] | publicKey | Pointer to the data array where the result public key should be stored. |
| [out] | plen | Length of the public key |
| [in] | privateKey_oid | an Object ID of a slot, where the newly generated key should be stored: Use one of the following slots: eSESSION_ID_1 eSESSION_ID_2 (Default) eSESSION_ID_3 eSESSION_ID_4 eDEVICE_PRIKEY_1 eDEVICE_PRIKEY_2 eDEVICE_PRIKEY_3 eDEVICE_PRIKEY_4 |
| [out] | privateKey | [Optional] Pointer to the data array where the result private key should be stored. |
| [out] | prlen | [Optional] Length of the private key. |
| 0 | If function was successful. |
| 1 | If the operation failed. |
|
inline |
| int32_t IFX_OPTIGA_TrustM::getCertificate | ( | uint8_t | certificate[], |
| uint16_t & | certificateLength | ||
| ) |
Get the Infineon OPTIGA Trust M device certificate.
The function retrieves the public X.509 certificate stored in the Infineon OPTIGA Trust M device. This certificate and the contained public key can be used to verify a signature from the device. In addition, the receiver of the certificate can verify the chain of trust by validating the issuer of the certificate and the issuer's signature on it.
| [out] | certificate | Pointer to the buffer that will contain the output. |
| [out] | certificateLength | Pointer to the variable that will contain the length. |
| 0 | If function was successful. |
| 1 | If the operation failed. |
|
inline |
This function returns the current limitation, which holds the maximum value of current allowed to be consumed by the OPTIGA™ Trust M across all operating conditions.
Default value 0x06
| [out] | currentLim | Reference where the value will be stored |
| 0 | If function was successful. |
| 1 | If the operation failed. |
|
inline |
This function returns the last error code.
| [out] | errorCodes | Pointer where the value will be stored |
| [out] | errorCodesLength | Pointer where the length of the value is stored |
| 0 | If function was successful. |
| 1 | If the operation failed. |
| int32_t IFX_OPTIGA_TrustM::getPublicKey | ( | uint8_t | publickey[68] | ) |
Get the Infineon OPTIGA Trust M device certificate public key.
The function retrieves the public X.509 certificate stored in the Infineon OPTIGA Trust M device and extracts the public key from it. Work for Certificates based on NIST P256 curve
| [out] | publickey | Pointer to the buffer where the public key will be stored. Should 68 bytes long. 64 bytes for the key and 4 bytes for the encoding BitString Format (0x03, 0x42, 0x00) + Compression format (0x04) + Public Key (64 bytes) |
| 0 | If the function was successful. |
| 1 | If the operation failed. |
| int32_t IFX_OPTIGA_TrustM::getRandom | ( | uint16_t | length, |
| uint8_t | random[] | ||
| ) |
Get a random number.
The function retrieves a cryptographic-quality random number from the OPTIGA device. This function can be used as entropy source for various security schemes.
| [in] | length | Length of the random number (range 8 to 256). |
| [out] | random | Buffer to store the data. |
| 0 | If function was successful. |
| 1 | If the operation failed. |
Generate Random -
|
inline |
This function returns the Coprocessor UID value. Length is 27, where First 25 bytes is the unique hardware identifier Last 2 bytes is the Embedded Software Build Number BCD Coded
| [out] | uniqueID | Pointer where the value will be stored |
| [in] | ulen | Pointer where the length of the value is stored |
| 0 | If function was successful. |
| 1 | If the operation failed. |
| int32_t IFX_OPTIGA_TrustM::pairMCU | ( | void | ) |
This function pairs the Host MCU and the OPTIGA Trust M This function by default works only with samples which have Pres-shared secret data object unlocked for modification YOu can though pair devices and then lock this dataobject afterwards.
| 0 | If function was successful. |
| 1 | If the operation failed. |
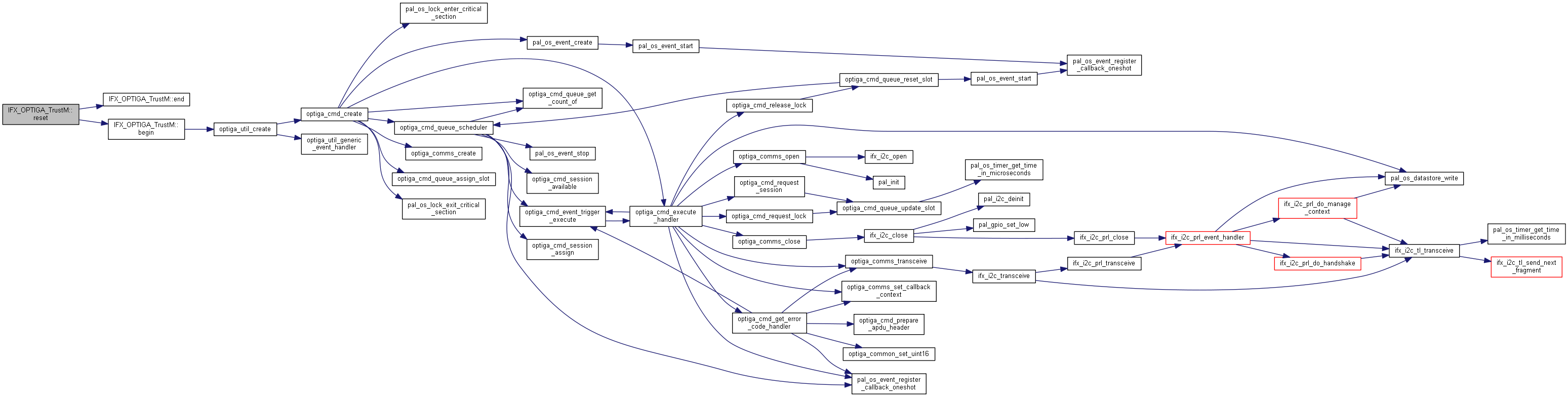
| int32_t IFX_OPTIGA_TrustM::reset | ( | void | ) |
This function resets the Infineon OPTIGA Trust M. This helps to recover the connection to the optiga once it got lost. (Indicator: 1 is returned by any other function)
| 0 | If function was successful. |
| 1 | If the operation failed. |
|
inline |
This function sets the sleep mode activation delay. Valid values are 0x06 - 0x0F or 6 mA - 15mA
| [in] | currentLim | The value that will be set |
| 0 | If function was successful. |
| 1 | If the operation failed. |
| int32_t IFX_OPTIGA_TrustM::sha256 | ( | uint8_t | dataToHash[], |
| uint16_t | dlen, | ||
| uint8_t | hash[32] | ||
| ) |
This function calculates SHA256 hash of the given data.
| [in] | dataToHash | Pointer to the data |
| [in] | dlen | Length of the input data |
| [out] | p_out | Pointer to the data array where the final result should be stored. Must be defined. |
| 0 | If function was successful. |
| 1 | If the operation failed. |
|
inline |
This function generates a shared secret based on Elliptic Curve Diffie-Hellman Key Exchange Algorithm This functions works in several modes. In general for such functions you need to specify following: elliptic curve type, private key, public key, result shared secret. Different functions listed below assume you don't need various parts of this input as you use internally stored values #1 sharedSecret(p_pubkey) - Private Key is taken from the first private keys slot. NISTP256 Curve is used #2 sharedSecret(priv_oid, p_pubkey) - Works like #1, but you can specifiy which slot to use. #3 sharedSecret(priv_oid, ssec_oid, p_pubkey) - Works like #1, but you can specifiy which slot to use for the private key and for the shared secret. #4 sharedSecret(curve_type, p_pubkey) - Works like #1, but you can define a curve type: "secp256r1" or "secp384r1" #5 sharedSecret(curve_type, priv_oid, p_pubkey) - Works like #2, but you can define a curve type: "secp256r1" or "secp384r1" #6 sharedSecretWithExport(p_pubkey, p_out) - Works like #1, but exports the result in p_out #7 sharedSecretWithExport(curve_type, p_pubkey, p_out) - Works like #5, but additionally you can define curve type of the publick key
This Shared secret can be used until the Session Context will be flashed, either after an application restart or a reset
| [in] | curveName | Curve name. The following are supported: "secp256r1" (Deafult) "secp384r1" |
| [in] | oid | Object ID defines which slot will be used as input and output Use one of the following slots: eSESSION_ID_1 eSESSION_ID_2 (Default) eSESSION_ID_3 eSESSION_ID_4 |
| [in] | publicKey | A pointer to a public key |
| [in] | plen | Length of a public key |
| [out] |
|
inline |
|
inline |
|
inline |
|
inline |
|
inline |
|
inline |
This function verifies an ECDSA signature. This functions works in two modes, either use internal OID where a public key is stored or you can give your own public key as an input
| [in] | hash | Pointer to the hash |
| [in] | hashLength | Length of the input data |
| [in] | publicKey_oid | [Optional] Object ID defines which slot will be used to verify the signature. The slot should contain a public key certificate starting with internat 0xC0 byte. For more information please refere to the datasheet documents. Default is the first slot. Possible values are: eDEVICE_PUBKEY_CERT_IFX (Default) eDEVICE_PUBKEY_CERT_PRJSPC_1 eDEVICE_PUBKEY_CERT_PRJSPC_2 eDEVICE_PUBKEY_CERT_PRJSPC_3 |
| [in] | signature | Pointer to the data array where the final result should be stored. |
| [in] | signatureLength | Length of the output data. Will be modified in case of success. |
| [in] | pubKey | A pointer to the public key to be used for the verification |
| [in] | plen | Length of the public key to be used for the verification |
| 0 | If function was successful. |
| 1 | If the operation failed. |
|
inline |
|
inline |
| int32_t IFX_OPTIGA_TrustM::verifySignatureECDSA | ( | uint8_t | hash[], |
| uint16_t | hashLength, | ||
| uint8_t | signature[], | ||
| uint16_t | signatureLength, | ||
| uint16_t | publicKey_oid | ||
| ) |
This function verifies an ECDSA FIPS 186-3 w/o hash signature. This functions works in two modes, either use internal OID where a public key is stored or you can give your own public key as an input
| [in] | hash | Pointer to the hash |
| [in] | hashLength | Length of the input data |
| [in] | publicKey_oid | [Optional] Object ID defines which slot will be used to verify the signature. The slot should contain a public key certificate starting with internat 0xC0 byte. For more information please refere to the datasheet documents. Default is the first slot. Possible values are: eDEVICE_PUBKEY_CERT_IFX (Default) eDEVICE_PUBKEY_CERT_PRJSPC_1 eDEVICE_PUBKEY_CERT_PRJSPC_2 eDEVICE_PUBKEY_CERT_PRJSPC_3 |
| [in] | signature | Pointer to the data array where the final result should be stored. |
| [in] | signatureLength | Length of the output data. Will be modified in case of success. |
| [in] | pubKey | A pointer to the public key to be used for the verification |
| [in] | plen | Length of the public key to be used for the verification |
| [in] | ecc_key_type | Public key ECC curve type |
| 0 | If function was successful. |
| 1 | If the operation failed. |
Verify RSA signature using public key from host
| int32_t IFX_OPTIGA_TrustM::verifySignatureECDSA | ( | uint8_t | hash[], |
| uint16_t | hashLength, | ||
| uint8_t | signature[], | ||
| uint16_t | signatureLength, | ||
| uint8_t | pubKey[], | ||
| uint16_t | plen, | ||
| optiga_ecc_curve_t | ecc_key_type | ||
| ) |
Verify RSA signature using public key from host
| int32_t IFX_OPTIGA_TrustM::verifySignatureRSA | ( | uint8_t | hash[], |
| uint16_t | hashLength, | ||
| uint8_t | signature[], | ||
| uint16_t | signatureLength, | ||
| uint16_t | publicKey_oid | ||
| ) |
This function verifies an RSA signature. This functions works in two modes, either use internal OID where a public key is stored or you can give your own public key as an input
| [in] | hash | Pointer to the hash |
| [in] | hashLength | Length of the input data |
| [in] | publicKey_oid | [Optional] Object ID defines which slot will be used to verify the signature. The slot should contain a public key certificate starting with internat 0xC0 byte. For more information please refere to the datasheet documents. Default is the first slot. Possible values are: eDEVICE_PUBKEY_CERT_IFX (Default) eDEVICE_PUBKEY_CERT_PRJSPC_1 eDEVICE_PUBKEY_CERT_PRJSPC_2 eDEVICE_PUBKEY_CERT_PRJSPC_3 |
| [in] | signature | Pointer to the data array where the final result should be stored. |
| [in] | signatureLength | Length of the output data. Will be modified in case of success. |
| [in] | pubKey | A pointer to the public key to be used for the verification |
| [in] | plen | Length of the public key to be used for the verification |
| [in] | rsa_key_type | Public key RSA type |
| 0 | If function was successful. |
| 1 | If the operation failed. |
Verify RSA signature using public key from host
| int32_t IFX_OPTIGA_TrustM::verifySignatureRSA | ( | uint8_t | hash[], |
| uint16_t | hashLength, | ||
| uint8_t | signature[], | ||
| uint16_t | signatureLength, | ||
| uint8_t | pubKey[], | ||
| uint16_t | plen, | ||
| optiga_rsa_key_type | rsa_key_type | ||
| ) |